Monokee, a next-generation Identity and Access Management (IAM) platform, leverages its innovative Visual Identity Orchestrator (VIO) to streamline integrations with various identity providers. This technical deep-dive explores the seamless integration between Monokee and Microsoft Entra, enabling near-instantaneous user provisioning through a series of well-defined API calls – a stark contrast to the traditionally complex and time-consuming IAM integrations.
12 posts tagged with "Monokee"
View All TagsSimple Identity Orchestration & Secure Face Verification On Any Device | iProov + Monokee
Monokee & iProov Partnership

Monokee and iProov are now collaborating to take another leap forward in authentication technology. We have seamlessly integrated iProov’s cutting-edge face verification capabilities as an innovative authentication method within Monokee’s low/no-code Identity and Access Management (IAM) identity orchestration platform.
In this article, we'll explain how iProov and Monokee's combined technologies work together to enhance security and user experience, creating a frictionless, passwordless option for enterprises.
Monokee 4.0 Access Management Capabilities
Monokee’s Access Management capabilities cater to both internal and external users, addressing use cases across a wide range of applications and services. It offers centralized identity management, single sign-on, multi-factor authentication, and granular authorization controls. These features align with external trends such as the convergence of IAM features, SaaS adoption, passwordless authentication, adaptive access, and cybersecurity mesh.
Monokee 4.0 Decentralized Identity
The identity landscape is evolving from well-known identity federations to fully decentralized solutions. The new Decentralized Identity (DCI) paradigm was designed to solve the existing problems with paper-based IDs in the digital realm by shifting the models toward user-centric, trustworthy, and privacy-preserving ones.
Monokee 4.0 Identity Governance and Administration
Monokee offers a potent solution with robust capabilities that are in line with the fundamental IGA functionalities. It provides inherent support for identity lifecycle management, ensuring that users have appropriate access when needed. The access request processes are streamlined, powered by the V.I.O. to further enhance access control and identity management. Monokee also features inherent capabilities for basic analytics and reporting, offering valuable insights into user activity and access patterns.
Monokee 4.0 Identity Orchestration
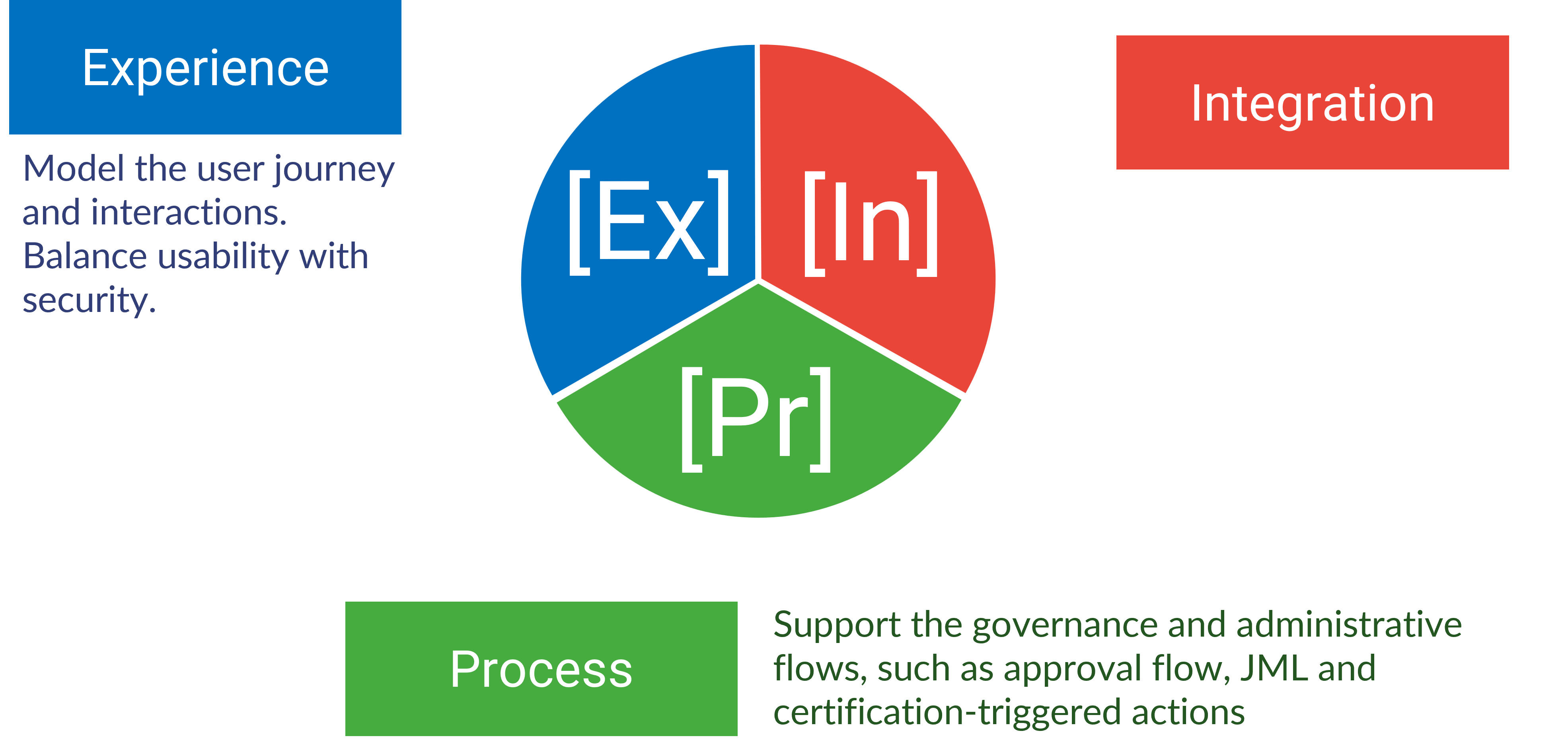
The term "identity orchestration" has become a popular buzzword, but its broad scope can sometimes lead to confusion. It encompasses a wide range of activities, from streamlining user journeys to integrating complex backend systems. This lack of clear definition can make it difficult for organizations to understand exactly what capabilities fall under this umbrella.
Monokee recognizes this need for disambiguation.
By breaking down identity orchestration into three distinct pillars – user experience, system integration, and enterprise process orchestration – we provide a clearer picture of the specific functionalities encompassed within this concept. This multi-faceted approach allows us to offer our clients targeted solutions that address their unique identity management needs.
Monokee identifies six enabling technologies for Identity Orchestration: a) User Journey Orchestration, b) Access Management, c) No/Low Code, d) Governance, e) Identity Consolidation, f) Decentralized Identities
Monokee 4.0 Privileged Access Management
Monokee only covers a minimum number of features in Privileged Access Management (PAM) and is designed to cover the requirements of small to medium organizations. For larger ones, Monokee supports full integration with third-party solutions such as CyberArk or Delinea. Monokee currently does not support password vaulting, activities control, in-session monitoring, privilege evaluation, or attestation. For these requirements, integration with a third-party partner is advised.
Add Toothpic as new passwordless MFA solution
Monokee's partner: Toothpic
Toothpic stands at the forefront of revolutionary authentication technology, introducing a cutting-edge approach that leverages the unique hardware characteristics of smartphones for unclonable identity verification. At its core, Toothpic addresses the escalating challenges of traditional authentication methods and forges a path towards a frictionless, passwordless identity and access management (IAM) framework.
Add Salesforce as Relying Party OpenID Connect
Accessing Salesforce through the OpenID Connect protocol
One of the most widely used protocols for implementing federated access is the OpenID Connect protocol. As with SAML, OpenID Connect allows access to an application (Relying Party - RP) by delegating authentication to an external provider (OpenID Provider - OP).
Monokee implements all the dictates of an OpenID Provider, in this regard it has also acquired full certification as OpenID Provider, as can be seen from the official website of the OpenID Fundation at this link.
The following article discusses how to integrate Salesforce and Monokee using the OpenID Connect protocol. Salesforce will play the part of the Relying Party while Monokee will play the part of the OpenID Provider.
Add Delinea Secret Server as Service Provider SAML 2.0
How to use SAML 2.0 protocol to access Secret Server
Secret Server allows the use of SAML Identity Provider (IDP) authentication instead of the normal authentication process for single sign-on (SSO). To do this, SS acts as a SAML Service Provider (SP) and communicates with Monokee that's acting as a SAML IDP.




