Monokee’s Access Management capabilities cater to both internal and external users, addressing use cases across a wide range of applications and services. It offers centralized identity management, single sign-on, multi-factor authentication, and granular authorization controls. These features align with external trends such as the convergence of IAM features, SaaS adoption, passwordless authentication, adaptive access, and cybersecurity mesh.
Access Management
Monokee is an all-encompassing access management suite, designed to meet the demands of today’s decentralized and dynamic environment. It provides core functionalities for both workforce and B2C users, including centralized identity management through directory services, seamless single sign-on (SSO) for streamlined access, robust user authentication with widely accepted multi-factor authentication (MFA) methods, and granular authorization controls.
Monokee stands out by supporting portable identities, offering integration with established providers like social media and cloud services, and backing emerging decentralized identity solutions. This flexibility broadens your reach and caters to a wide range of user needs.
For B2B partners, Monokee simplifies registration and permission management. For B2C customers, it enhances user experience through self-service options, activity logging, and native consent collection.
Monokee’s authorization and adaptive access features allow for dynamic decision-making based on contextual data and risk evaluation. Its extensibility empowers you to integrate additional IAM and security tools, customize experiences, and embed controls into custom applications.
Security is further enhanced with phishing-resistant MFA methods, compromised password mitigation, and robust API access controls. While threat reporting and ITDR are future additions, current functionalities enable you to define strict risk-based policies, audit access, and mitigate potential risks.
Monokee aligns with identity-first principles, offering adaptability, integration, and extensibility. This paves the way for a secure, interoperable, and distributed identity fabric.
Critical Capabilities
Identities Repository
Monokee goes beyond the minimum requirements of a directory service by providing a comprehensive identity management solution for both workforce and CIAM. It offers advanced features for identity synchronization, SCIM support, access governance, self-service, and identity-based security.
Users management
Monokee acts as a centralized repository for identities, storing custom attributes, roles, groups, and more. Within each user, group, and application, detailed properties are available and configurable.
Identity synchronization and integration
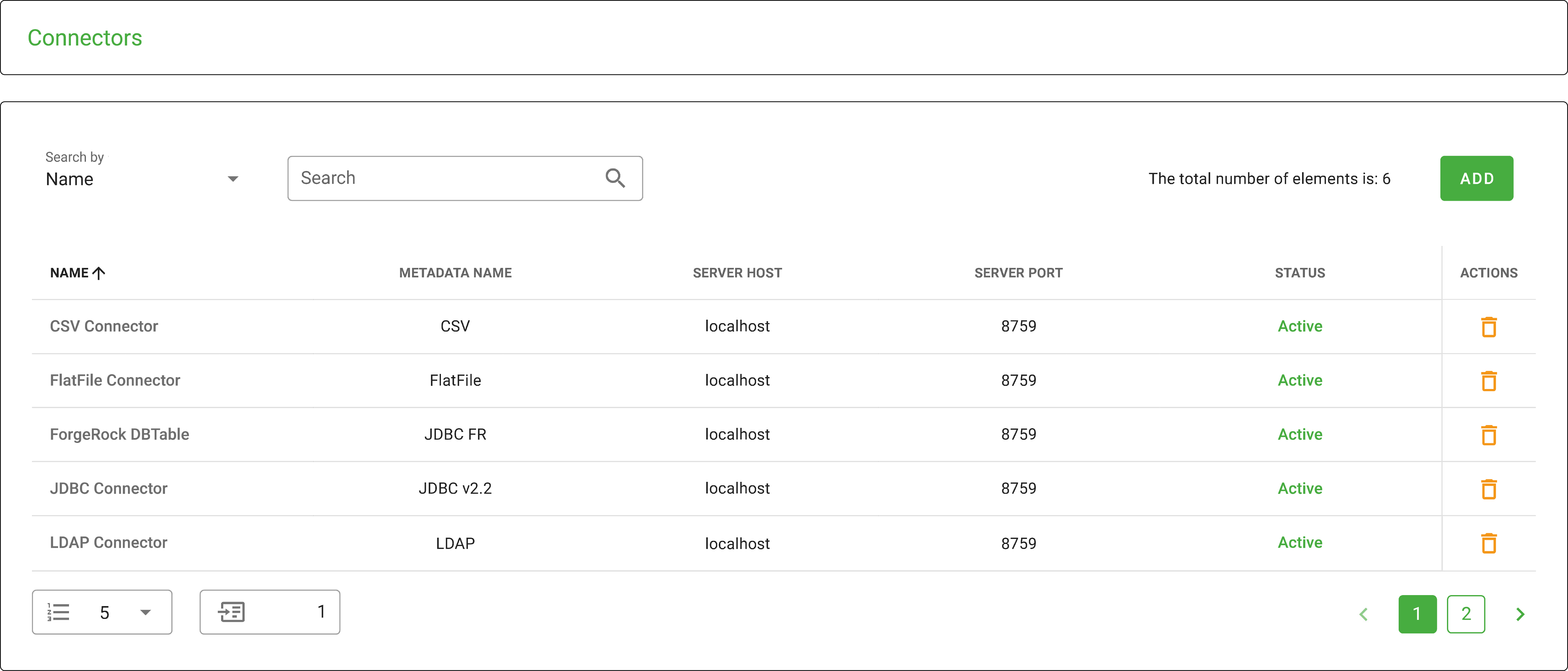
Monokee offers connectors to synchronize identities with existing directories like Active Directory, LDAP, and HR systems. This ensures consistent and up-to-date information across platforms. Monokee supports inbound and outbound SCIM provisioning, allowing applications to automatically request and receive user attributes directly.
General management
Monokee streamlines user lifecycle management, starting with smooth onboarding. Whether for employees or customers, automated workflows ensure they quickly gain access to appropriate applications based on their roles, groups, or specific attributes. Users can also participate in a self-service experience, registering, initiating access requests, and updating their profiles, all while reducing the burden on IT teams. Onboarding journeys can even be customized based on user types or departments for added flexibility. Concerning offboarding, Monokee automatically revokes access across connected applications upon termination, minimizing security risks from lingering access. Throughout the user lifecycle, dynamic access management plays a crucial role: Monokee employs role-based access control (RBAC) to assign privileges tailored to user roles, eliminating the need for manual configurations. Regular access reviews keep user access relevant and secure, while Just-in-Time provisioning offers temporary access for specific needs.
Identity-first security
Monokee natively integrates dynamic, context-aware controls for ensuring a quick an effective response to changes in risks and trust throughout the user journeys.
Identity Administration
Monokee offers native administrative tools for identity management and administration. A fully compliant SCIM interface is available in the Identity Manager to provide support for third party integrations. Users can be synchronized to and from Monokee as well as third party resources with support for context-based workflows and custom provisioning and/or deprovisioning. Fully automated flows can be integrated with general-purposes interactive ones.
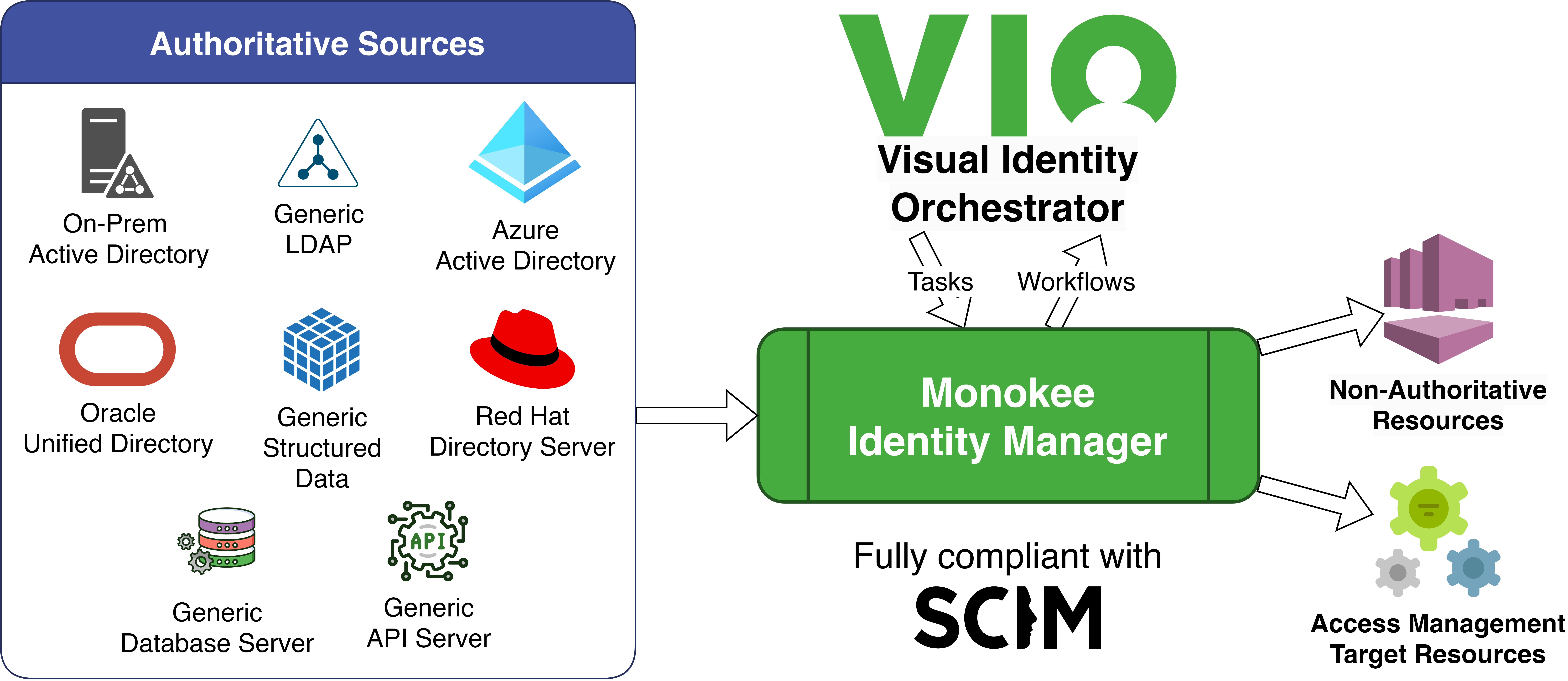
Multiple authoritative sources can be used to populate target resources, including Monokee user repository or third-party applications.
Single Sign-On (SSO) and Session Management
Monokee plays a hybrid role, depending on the process in which it is involved and the actor addressed and supports multiple protocols in each phase independently. For example, you can use a SAML application (SP) with Monokee as IdP but have the users come from another IdP using any given modern authentication protocol.
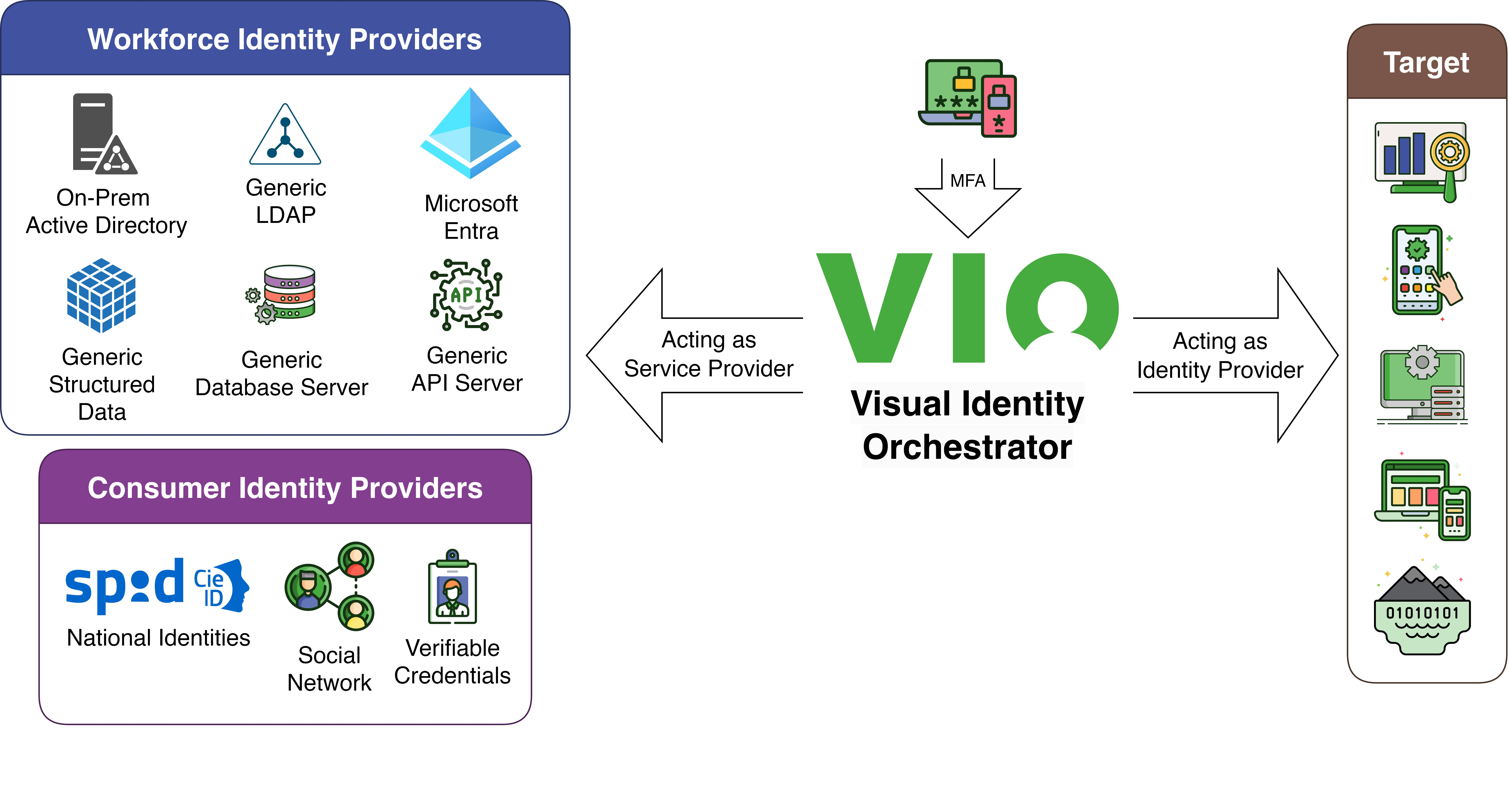
To achieve these bridging functionalities, Monokee extensively supports SSO protocols such as SAML 2.0, OAuth 2, OpenID Connect, JSON Object Signing and Encryption (JOSE), Simple Web Tokens, and mTLS. Custom authentication methods can be evaluated upon request. Monokee is also OpenID Certified (including for third-party-initiated OP).
Application Broker
Monokee supports apps integrated with modern and custom legacy (or not standard) authentication methods. Configurations for individual applications can be imported, exported, and provided as a template.
Your application, your rules: individual applications can be protected by customizable access policies.
Administrators can use data from users, roles, custom attributes, custom scripts, and external data sources to make a decision. Individual applications can be associated directly with users but also with groups, and, in addition to the classic RBAC scheme, custom attributes may be valorized statically (i.e., based on individual users’ attributes or groups) but also dynamically (i.e., based on APIs, policies, or runtime values).

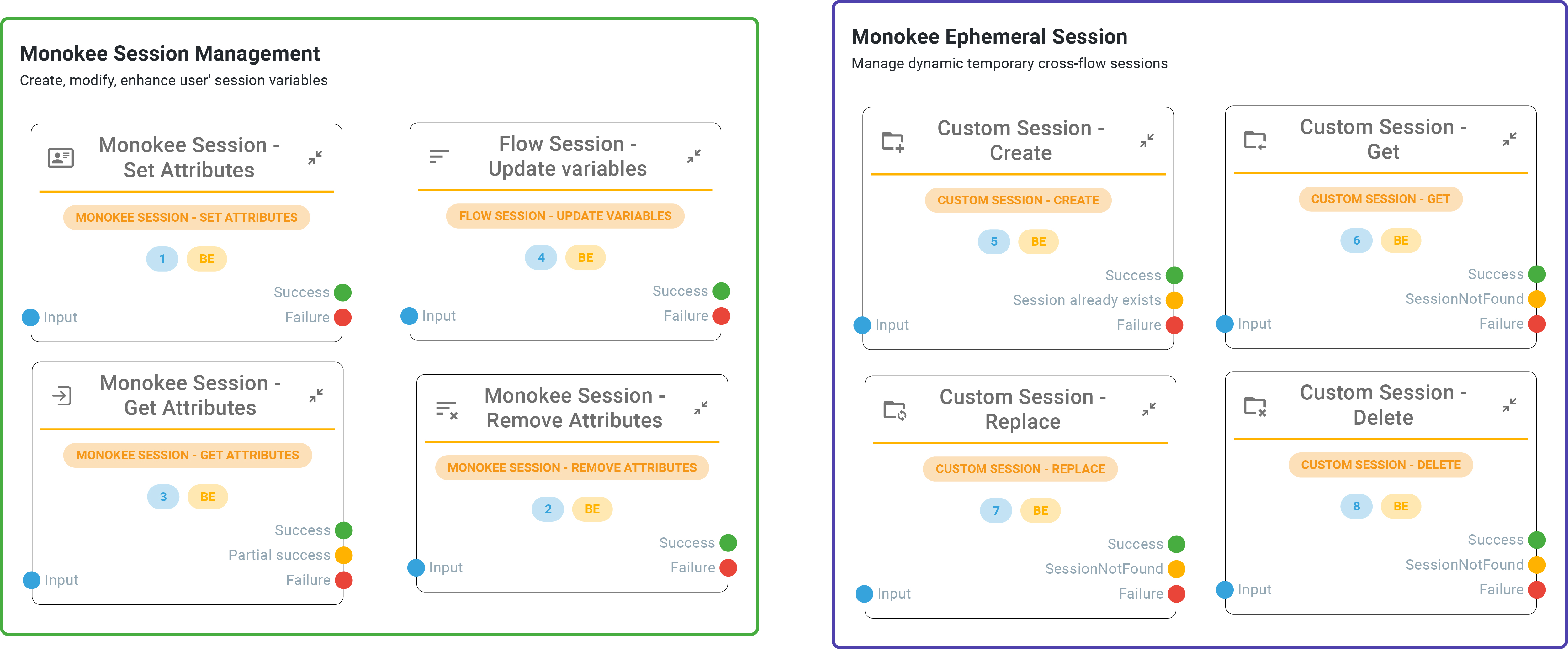
Session Management
Monokee sessions are completely customizable directly from the V.I.O. with the corresponding nodes. Monokee’s V.I.O. offers a robust session management system. This system is designed with a high degree of capabilities and granularity, enabling it to regulate the state of user sessions during interactions with applications. The platform can manage session durations by issuing and refreshing time-limited access tokens or cookies. This feature ensures that user sessions remain secure and active only for the intended period. Additionally, the platform has the capability to terminate sessions, providing an extra layer of security and control. Users can manage their sessions across multiple applications from a single interface, enhancing usability and efficiency.
User Authentication
Monokee out-of-the-box offer includes core AM functionalities for workforce, B2B, and B2C use cases. Along with core user-authentication methods and classic MFAs, Monokee offers mitigation controls for common threats and general passwordless approaches. Enforcing a solid MFA strategy for a more secure business environment is extremely important but nonetheless often ignored. To ease enterprises in rolling out mandatory MFA for all accounts, Monokee natively integrates several authentication factors:
- One-Time Password (OTP), both time-based (TOTP) or HMAC-based (HOTP).
- SMS (discouraged as of 2017).
- Hardware tokens and security keys.
- Device attestation and device pinning.
- WebAuthN and FIDO2, including multi-device passkeys.
- Biometrics, Know Your Customer (KYC), and Anti-Money-Laundering (AML) providers.
- Decentralized Identities with full support for W3C Verifiable Credentials and Verifiable Presentations.
Monokee integrates with multiple vendors worldwide to ensure optimal coverage and cutting-edge technologies.
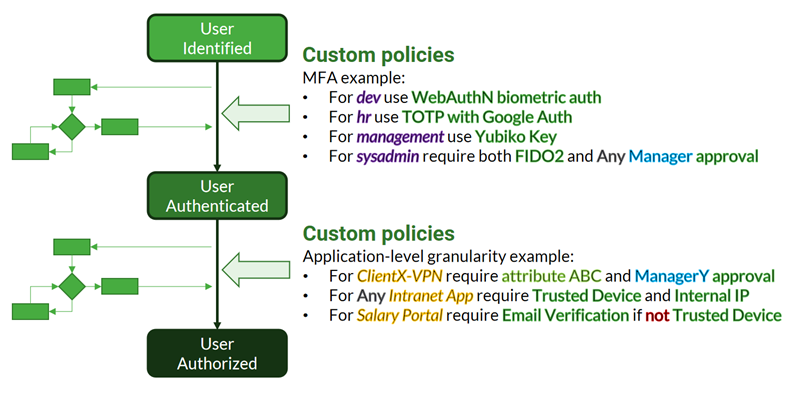
Authorization
Monokee supports dynamic and configurable authorization approaches: it is possible to combine multiple conditions to guarantee authorized access to the applications. The figure that follows summarizes some examples of custom policies that can be designed within Monokee.
Additional Capabilities
Portable Identities and Business-to-Business (B2B)
Monokee allows users to leverage their existing digital identities, such as those from government agencies, banks, and communication service providers, to authenticate themselves in various online environments.
This capability is further enhanced with Business-to-Business (B2B) dedicated connectors: businesses can invite and register partners and manage their permissions through delegated administration functionalities or directly from within their default user journeys, while still retaining the options of managing the access rights of multiple external partners.
In Monokee, these capabilities are included out-of-the-box, including delegated administrator roles and delegated administrators. Just-in-time provisioning is also supported during this process.
Business-to-Consumer (B2C)
Monokee offers self-service functionalities for both administrators and final users including streamlined onboarding (automated workflows to expedite provisioning and access assignment, roles, and permissions), offboarding (swift deprovisioning and account termination, including data removal), application access (requests, role-based permissions, and attributes-based permissions), and data processing processes (consent collection, forced checkpoints, export rules, and data sharing flows).
With the V.I.O., Monokee empowers a shift towards a user-centric, identity-first, IAM approach to bolster efficiency, compliance, and a positive user experience.
Continuous Adaptive Trust (C.A.T.) and Threat Response
Enforcing a solid MFA strategy for a more secure business environment is extremely important but nonetheless often ignored. To ease enterprises in rolling out mandatory MFA for all accounts, Monokee natively integrates several authentication factors:
- One-Time Password (OTP), both time-based (TOTP) or HMAC-based (HOTP).
- SMS (discouraged as of 2017).
- Hardware tokens and security keys.
- WebAuthN and FIDO2.
- Biometrics, Know Your Customer (KYC), and Anti-Money-Laundering (AML) providers.
Monokee integrates with multiple vendors worldwide to ensure optimal coverage and cutting-edge technologies.
Unfortunately, a blind count of the authentication factors asked of the user is a naïve approach. Monokee enables security engineers to build custom policies for dynamic risk and trust management that include runtime conditions and behavioral parameters to achieve Continuous Adaptive Trust (CAT). With Monokee, you can move from MFA to CAT, integrating passwordless user journeys where the trust in the user identity is continuously adapted and evaluated.
Custom factors can increase security while reducing the frequency of additional authentication steps. Different entry barriers can be designed on security levels and threat indicators, enabling frictionless access to low-sensitivity areas while guaranteeing a security assurance level. CAT factors include user identity, access context, reputation analysis, and anomaly detection.
Extensibility and customizations
Integrate third party solutions via RESTful APIs, both as input and output of Monokee’s flows. Each user journey provides full compatibility with HTTP methods to create general purpose CRUD-like operations.
From the V.I.O., multiple utilities nodes offer native and external signals integration with no-code approach to enable custom-built applications and APIs. Snippets for flows and nodes can be copy-pasted across environments and from the official documentation.
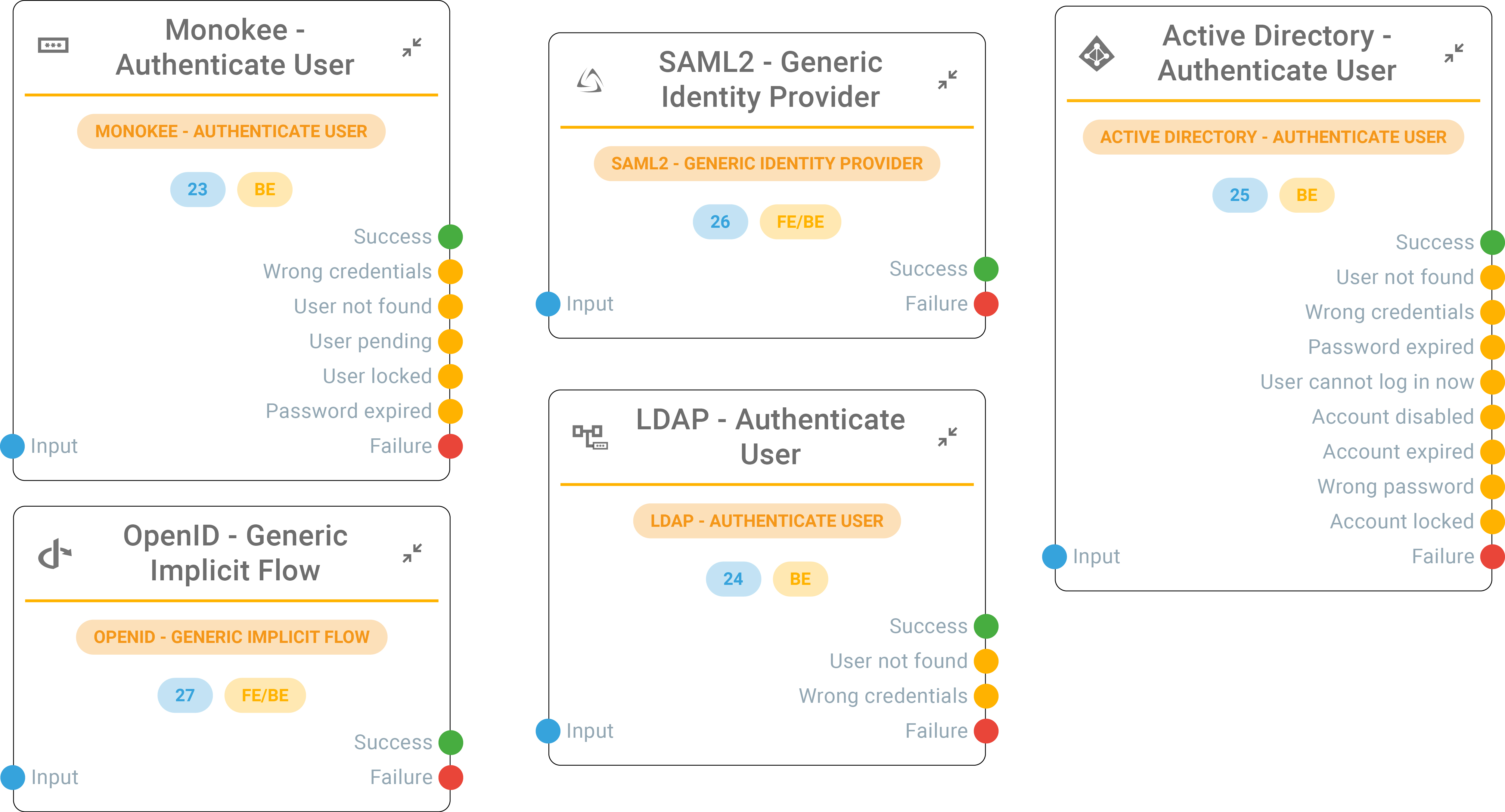
An example of Access Flow
This description details the initial steps of a user journey within Monokee's Identity Orchestration platform. It highlights the decision-making process based on user authentication status.
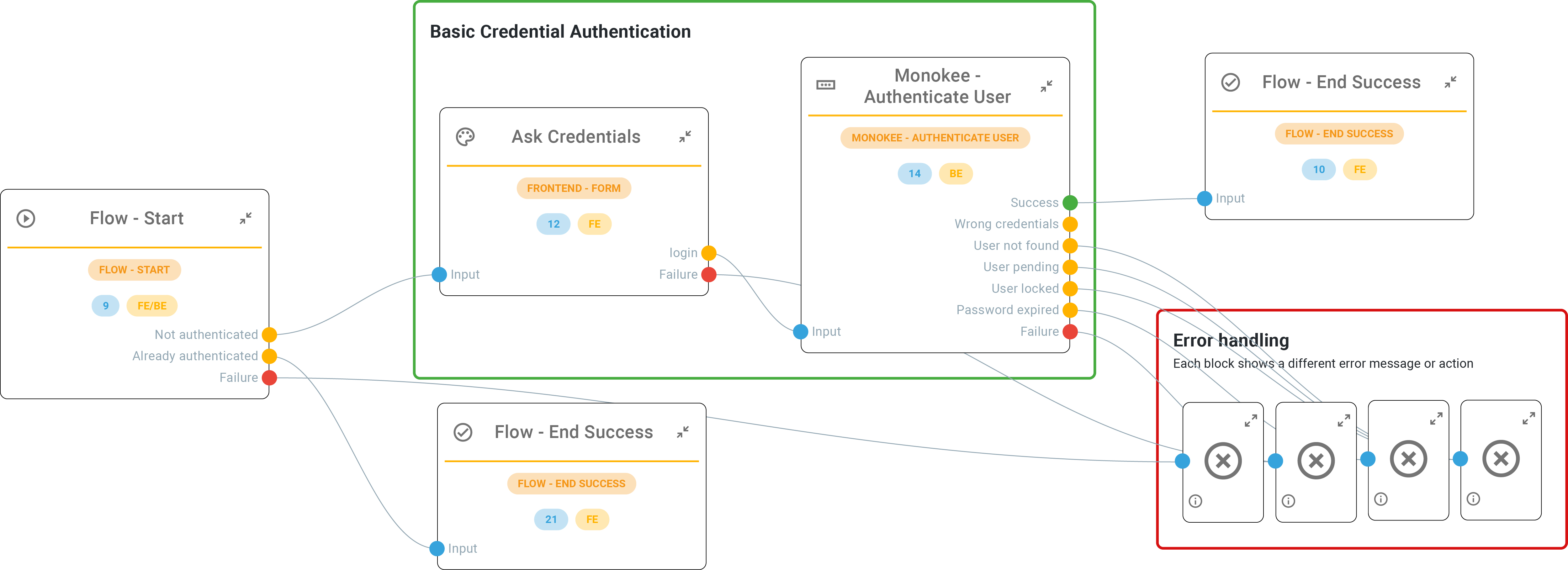
Here's a breakdown:
- Starting Node: This is the entry point for all user journeys. A user lands here upon initiating the access request.
- Authentication Check: The system verifies if the user is already authenticated (e.g., has a valid session).
- Authenticated User: If the user is already authenticated, they bypass the authentication steps and proceed directly to the target application (End Success).
- Unauthenticated User: If the user isn't authenticated, the journey progresses to the next step.
- Frontend Form Ask Credentials: This node presents a login form to the user, with username and password fields.
- User Input: The user enters their credentials and submits the login form. The values are stored as variables for later usage.
- Monokee Authenticate User: This node receives the submitted credentials and performs the authentication process.
- Successful Authentication: If the credentials are valid, the user is authenticated, and the journey proceeds to the End Success node, granting access to the target application.
- Failed Authentication: If the credentials are incorrect, the user is directed to an error state labeled "Wrong credentials."
- Additional Error Exits: There are other potential exits:
- User Not Activated: This indicates a user account that hasn't been activated yet.
- User Locked: The user has been locked by an administrator or an automatic process.
- Password Expired: The user's password might have exceeded its validity period and needs resetting.
This example focuses on username/password authentication. Monokee supports other authentication methods (MFA, social logins) that would be integrated into this flow at different points.


