The identity landscape is evolving from well-known identity federations to fully decentralized solutions. The new Decentralized Identity (DCI) paradigm was designed to solve the existing problems with paper-based IDs in the digital realm by shifting the models toward user-centric, trustworthy, and privacy-preserving ones.
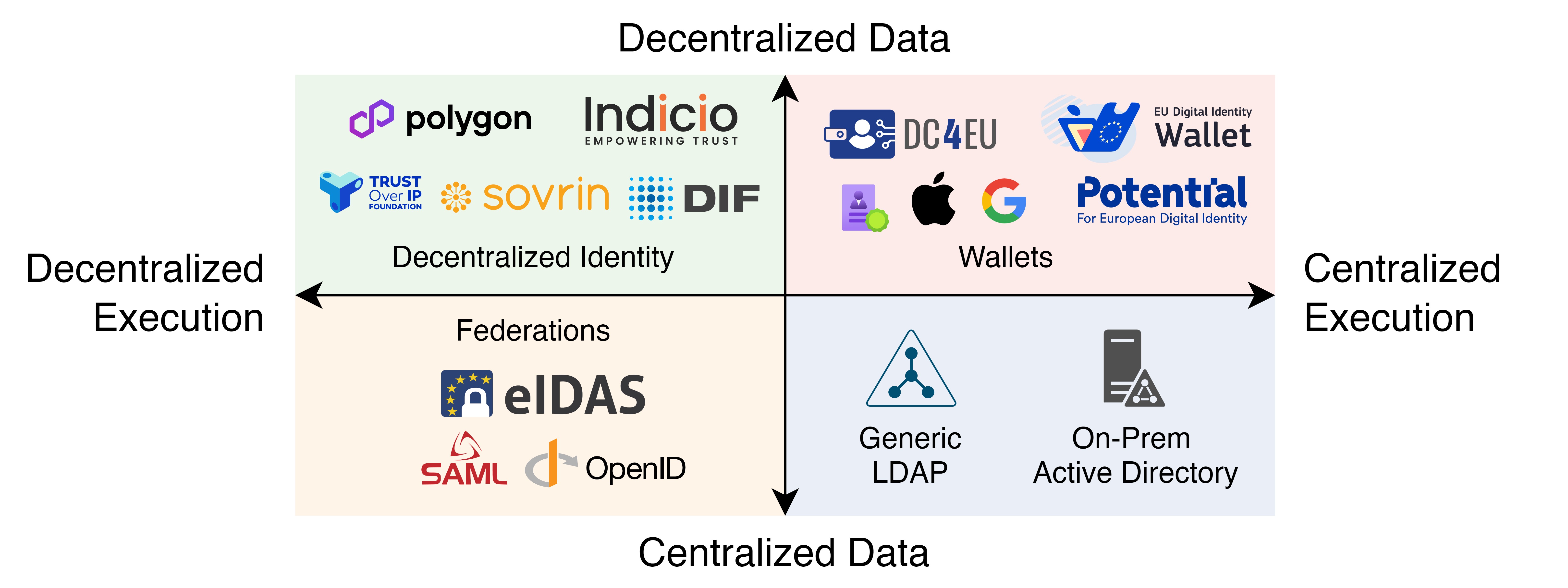
Trends show that a DCI model is becoming a new standard. Monokee has already dedicated resources to the new paradigm and is ready for DCI, offering the possibility to enable DCI solutions frictionlessly in any centralized context. Monokee is a trusted partner of multiple decentralized vendors and contributes to public projects and communities to streamline the adoption of decentralized identity technologies in enterprise environments.
Frequently Asked Questions about Decentralized Identity
Why should you care about Decentralized Identity? Nowadays, The European Union is pushing for the implementation of a universal wallet for digital attestation and credentials officially recognized across all the Member States using the decentralized paradigm. Estonia is the first country to use blockchain on a national level and is now moving its digital identity to a decentralized model. The European Research Council is funding four projects about new citizen digital identity solutions, and decentralization is one of the new key points when they speak about the next generation of secure digital wallets.
How does it work? The architecture and technical details may vary depending on the framework. Still, at its core is the concept of trustless trust, which is the idea of building trust chains that replace people, agents and intermediaries with software and distributed consensus. On top of that, individuals may decide precisely what information to share with which actors, often in the form of Zero-Knowledge Proofs (ZKPs) anonymous credentials.
Where can it be used? The correct answer is almost everywhere. Monokee enables seamless integration of distributed technologies in B2B and B2C services that can apply to conservative and innovative use cases such as the IoT and smart cities scenarios or generic autonomous projects.
What do you need? Surprisingly, with Monokee, you will not need anything else. The whole stack is already integrated to manage Decentralized Identifiers and Verifiable Credentials. In the first case, Monokee allows you to generate or import new Identifiers and define Issuers and Verifiers entities. In the second one, you can accept, issue, and verify standard W3C Verifiable Credentials (VCs). All these features are available with the support of the V.I.O.
What does Monokee do for Decentralized Identity? Monokee is natively integrated with some of the major technologies in the DCI and Web3 ecosystem, which are working on the Decentralized Identity issue. Among others, the integrated solutions are:
Monokee also supports Hyperledger Indy and Aries based technologies such as Sovrin and Indicio.
Monokee makes all these integrations and features readily available and accessible, making your entry or migration to this new paradigm effortless.
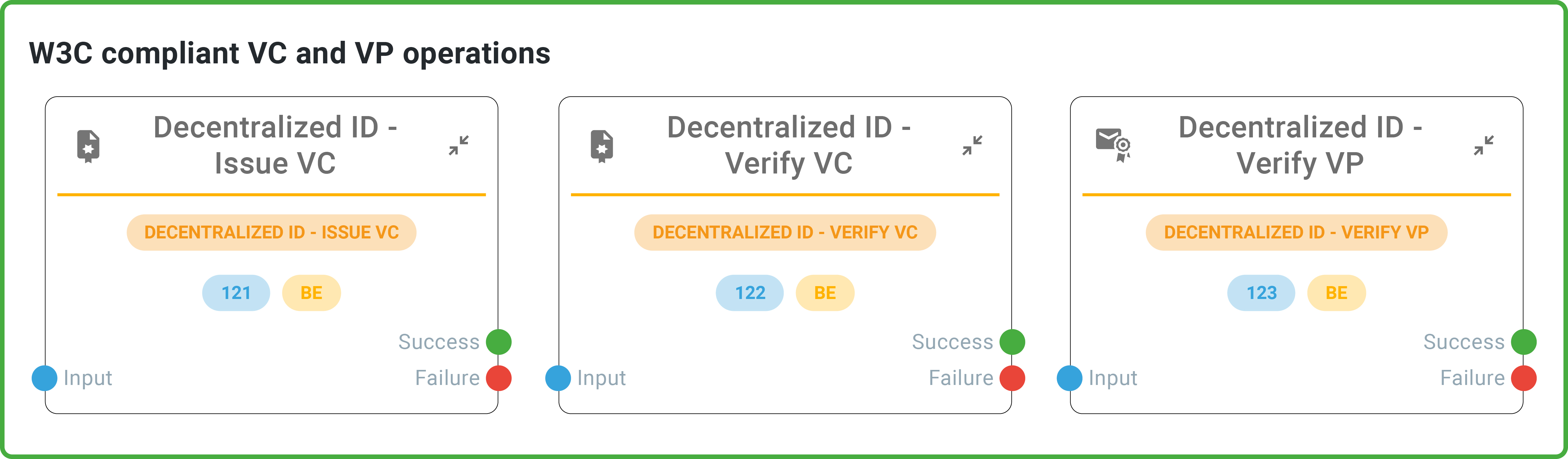
Decentralized Technologies applied
Just-in-time provisioning with verifiable presentations using native SSH
In this use case, Monokee supports two variants. The first one promotes the just-in-time provisioning of a user to a target system with explicit authorization from the user. On the other hand, the second variant enables the creation of the account based solely on the Verifiable Presentation created by the user. In both cases, the SSH protocol is left untouched, and the user does not obtain the credentials to access the target system, while still being able to connect via a connection gateway.
UNIX Pluggable Authentication Modules (PAM) provide a flexible way to plug-in different authentication mechanisms into existing applications like SSH. Monokee utilizes a custom PAM module to handle VP-based JIT provisioning within the SSH workflow.
In both cases, the SSH protocol is left untouched, and the user does not obtain the credentials to access the target system, while still being able to connect via a connection gateway.
Just-in-Time with explicit authorization
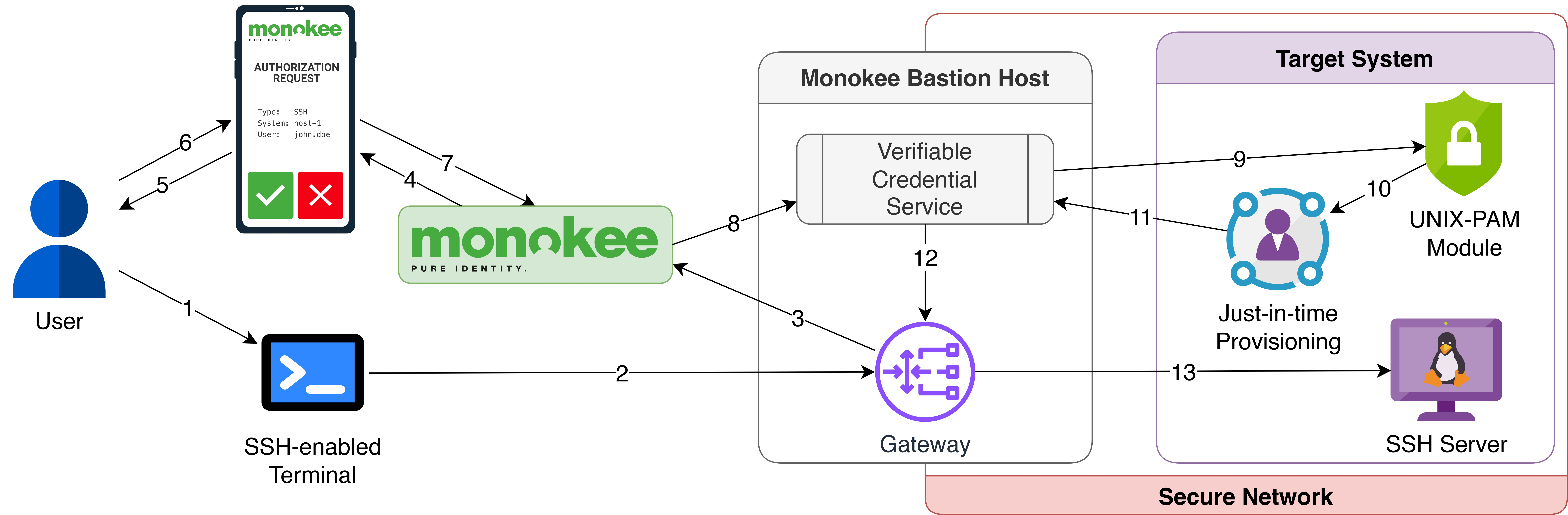
Steps:
- (1): The user opens a terminal to connect to host-1;
- (2): The SSH protocol initiates by connecting to the corresponding Monokee’s Gateway;
- (3): The Gateway requests Monokee for authentication and authorization;
- (4,5,6,7): A round trip for a Verifiable Presentation exchange is executed to approve the operation;
- (8): The Verifiable Presentation is shared to Monokee Credential Service;
- (9,10,11): The target system receives the Verifiable Presentation and performs the provisioning of the user, if required;
- (12,13): The gateway is notified that the operation has successfully completed and opens a connection with the target system with the correct user.
Just-in-Time with implicit authorization
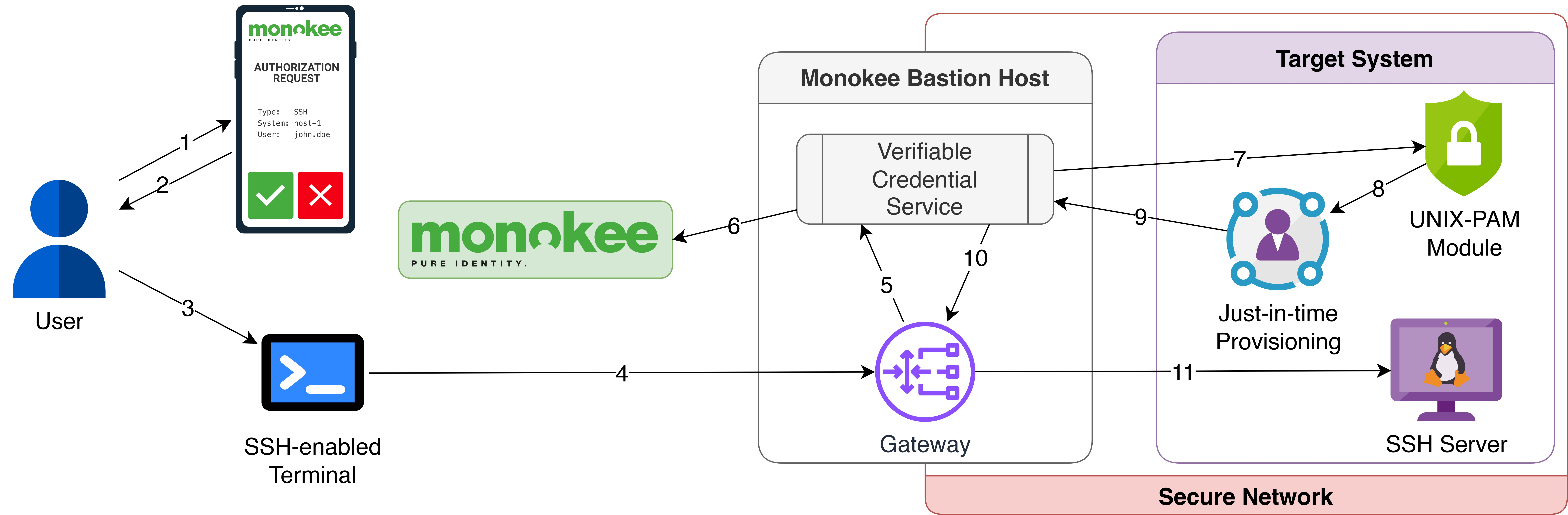
Steps:
- (1,2): The user generates a Verifiable Presentation with his Verifiable Credentials stating identity and general roles;
- (3): The user opens a terminal to connect to host-1;
- (4): The SSH protocol initiates by connecting to the corresponding Monokee’s Gateway;
- (5,6): The Verifiable Credential Service receives the Verifiable Presentation and verifies it, optionally checking with Monokee;
- (7,8,9): The target system provisions the user with the corresponding roles as required, gathering the information from the Verifiable Credentials included in the presentation;
- (10,11): The gateway is notified that the operation has successfully completed and opens a connection with the target system with the correct user.
Selective Disclosure and Zero-Knowledge Proofs
Using the PolygonID open-source SDK, Monokee leverages a new authentication method that enhances the security and privacy of both the users and the ecosystem. Using the Polygon Wallet, users can present only Zero Knowledge Proof about a specific request instead of a Verifiable Presentation where you must inevitably share your personal data. When you initialize your wallet, it generates a Decentralized Identifier that Monokee binds to the user profile. Hence, upon authentication, Monokee generates a request for proof-of-ownership for the DID linked with the user profile. The request is shared with the wallet either via QR code or push notifications and the user wallet must confirm it in Zero-Knowledge. As for the credentials issuance and storage in the wallet, Monokee directly integrates with PolygonID SDK for both issuance and upload to the user wallet. Monokee uses cases involve using this feature to manage access to specific resources or platform pages and it is entirely customizable in both VC content and style.
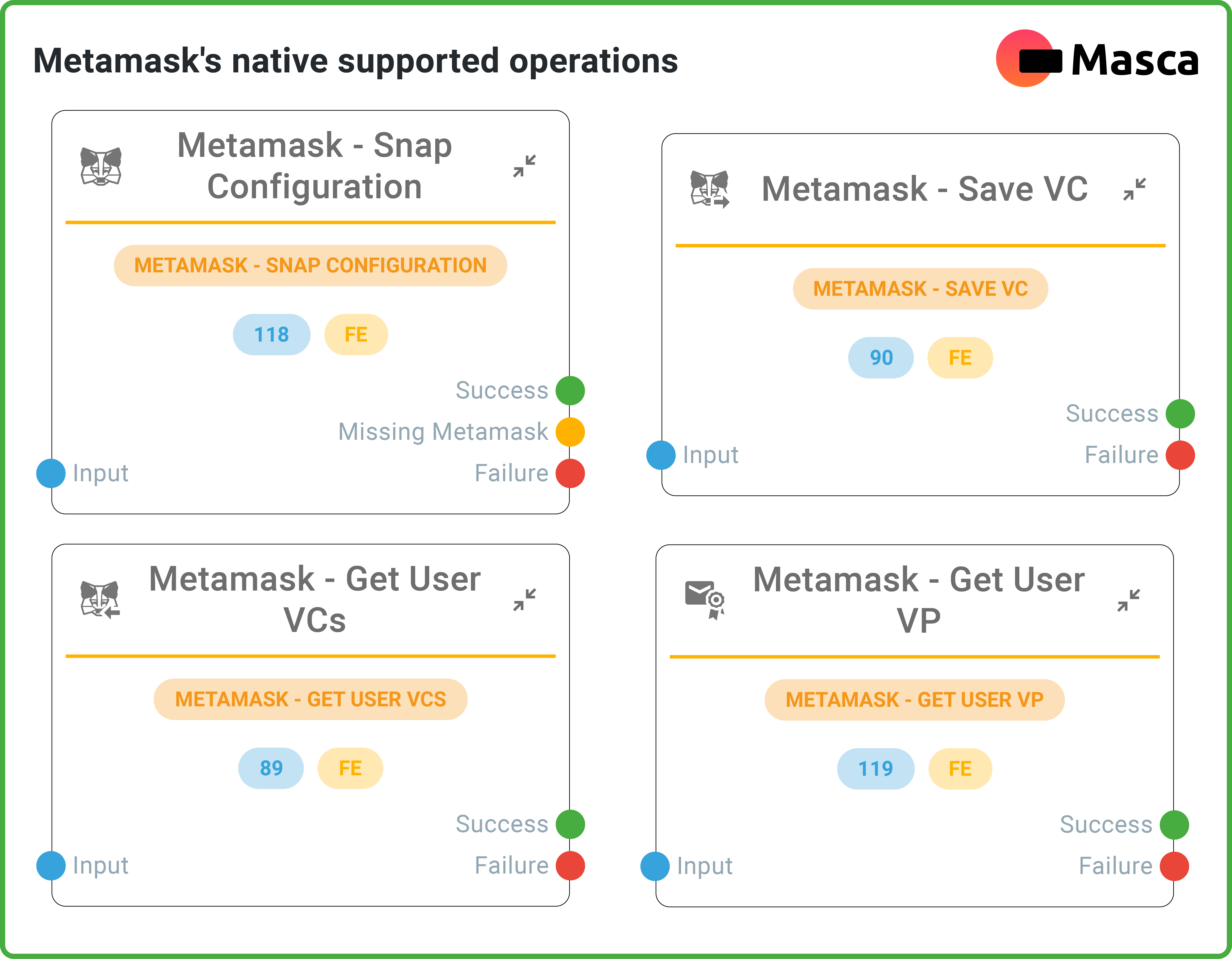
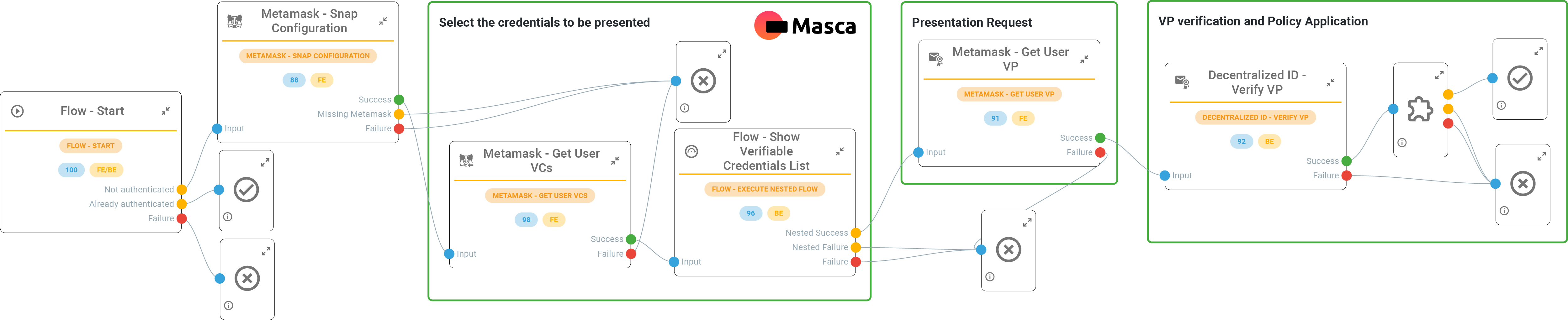
Metamask and Verifiable Credentials
Companies are quickly moving to a decentralized way of managing things, so Monokee has decided to use the most famous Ethereum wallet as a place to save credentials, adhering to the trend in Web 3.0 space to offer compatibility with a unique wallet that can manage everything in one place (both cryptocurrencies and verifiable credentials). By installing the Masca snap on your Metamask wallet, users have access to multiple Decentralized Identifiers and storage systems to store VCs. The DID keys are derived from the user wallet keys without the need to memorize or perform any action, thus providing a user-friendly solution already known by many Web 3.0 users. Similarly to other use cases, the DID is uniquely associated with a Monokee user, thus enabling information retrieval based on the DID proof of possession. Monokee issues W3C-compliant Verifiable Credentials signed by personalized DIDs, including generic did:key, did:web, did:sov, and did:cheqd. Each tenant and domain can define custom DIDs and register them to the correct chain through Monokee’s interface. Generated credentials and credentials requests are defined with W3C standards and aligned with OIDC4VCI and OIDC4VP drafts to ensure maximum compatibility with other technologies.
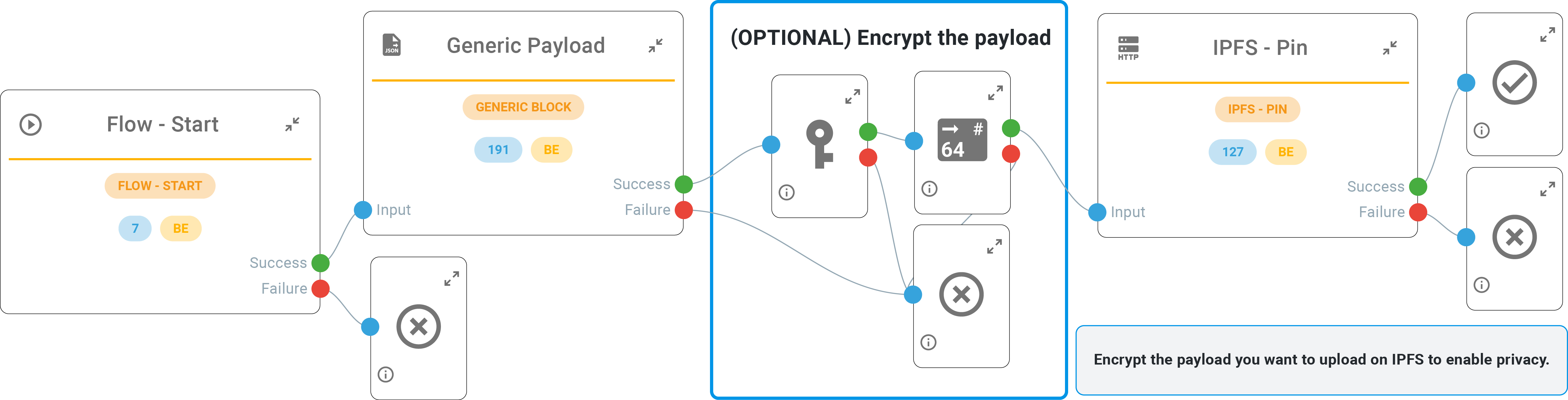
IPFS as a Tamper-Proof decentralized registry
To enable comprehensive auditing and logging of a specific activity, Monokee offers native integration with distributed storage solutions. Among other planned integrations, Monokee’s V.I.O. offers InterPlanetary File System (IPFS) nodes. IPFS is a decentralized technology that ensures the creation of tamper-proof records, fostering transparency and auditability. This “security by transparency” approach ensures that modifications are permanently recorded, ensuring both authenticity, integrity, and immutability of the records.