Monokee only covers a minimum number of features in Privileged Access Management (PAM) and is designed to cover the requirements of small to medium organizations. For larger ones, Monokee supports full integration with third-party solutions such as CyberArk or Delinea. Monokee currently does not support password vaulting, activities control, in-session monitoring, privilege evaluation, or attestation. For these requirements, integration with a third-party partner is advised.
Privileged remote access management
Monokee can be integrated with Zero-Trust solutions to grant just-in-time access to internal machines via RDP or Web HTML5 connections. Access can be granted temporarily and with customized flows that may include explicit policy acceptance, confirmation, or third-party approval.
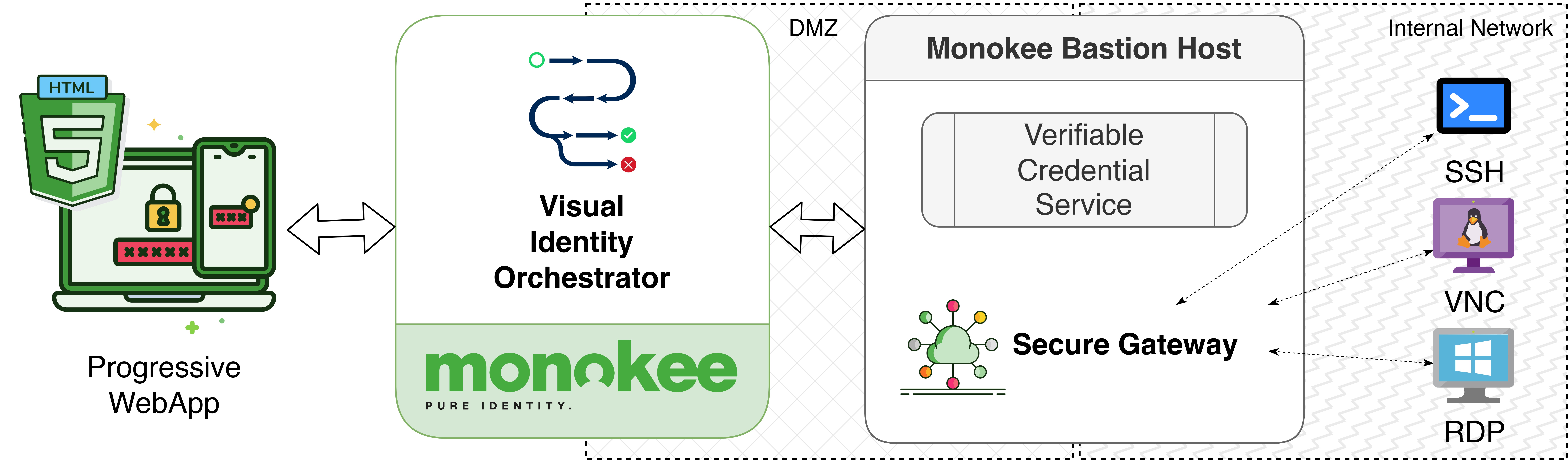
Native solution using Apache Guacamole
Apache Guacamole is a free and open-source remote desktop gateway (RDG) that provides secure and convenient access to remote desktops and applications from any web browser. It is a popular choice for enterprises of all sizes because it offers a number of security and operational benefits, including:
- Encryption of all traffic: Guacamole encrypts all traffic between the client (web browser) and the server, including the user's login credentials, keyboard input, and screen output. This protects sensitive data from being intercepted by attackers.
- Support for multiple remote desktop protocols: Guacamole supports a variety of remote desktop protocols, including RDP, VNC, and SSH. This allows users to access a wide range of remote desktops and applications, regardless of the underlying protocol.
- Easy to deploy and manage: Guacamole is easy to deploy and manage, even for organizations with limited IT resources. It is available as a pre-built appliance or as a software package that can be installed on a wide range of operating systems.
- Session recording: Guacamole can record user sessions, which can be used for troubleshooting, auditing, and security investigations.
- Session shadowing: Guacamole allows administrators to shadow user sessions, which can be used for training, support, and security monitoring.
- Integrations with other security tools: Guacamole can be integrated with other security tools, such as intrusion detection systems and security information and event management (SIEM) systems.
Partner solution using Delinea RAS and SS
The integration of DELINEA Remote Access Server (RAS) and Secret Server (SS) is a multi-faceted process that enhances the security and efficiency of remote access services. This integration is achieved on several levels, each contributing to a more streamlined and secure user experience.
Federated Authentication Using SAML
The first level of integration involves federated authentication using SAML. In this setup, Monokee acts as the Identity Provider (IdP), while Delinea Secret Server functions as the Service Provider (SP). This arrangement allows for secure and seamless authentication across different systems and platforms. A deep-dive technical integration is discussed in the blog post: Add Delinea Secret Server as Service Provider SAML 2.0.
APIs for Provisioning and User Management
The integration also leverages Application Programming Interfaces (APIs) for provisioning and user management. These APIs facilitate two key processes:
- Joiners, Movers, Leavers (JML) with Users, Roles, Groups: Monokee calls the Delinea API to perform tasks from the Visual Identity Orchestrator (VIO). This process involves managing users, assigning roles, and organizing groups, thereby ensuring that the right users have the right access at the right time.
- Synchronization of Users: Monokee, acting as the authoritative source, uses the VIO to keep synchronization on regular intervals. This ensures that user data is up-to-date across all platforms, enhancing security and reducing the risk of unauthorized access.
Finally, authenticated Monokee users will be automatically authenticated to Delinea RAS. They can see the list of available remote targets and download the configuration to be executed by the Privileged Access Manager installed locally. This provides a seamless user experience, reducing the need for multiple logins and enhancing productivity.
Third-party solution using CyberArk PAS
Monokee can be easily integrated with CyberArk using the API service provided. All features of CyberArk, such as in-session monitoring, in-session recording and in-session ending are supported thanks to the PSM module, which is tasked with fully controlling the endpoint. Starting a new session from Monokee is as easy as that, the endpoint target is initialized in just a few clicks with all supported CyberArk features.
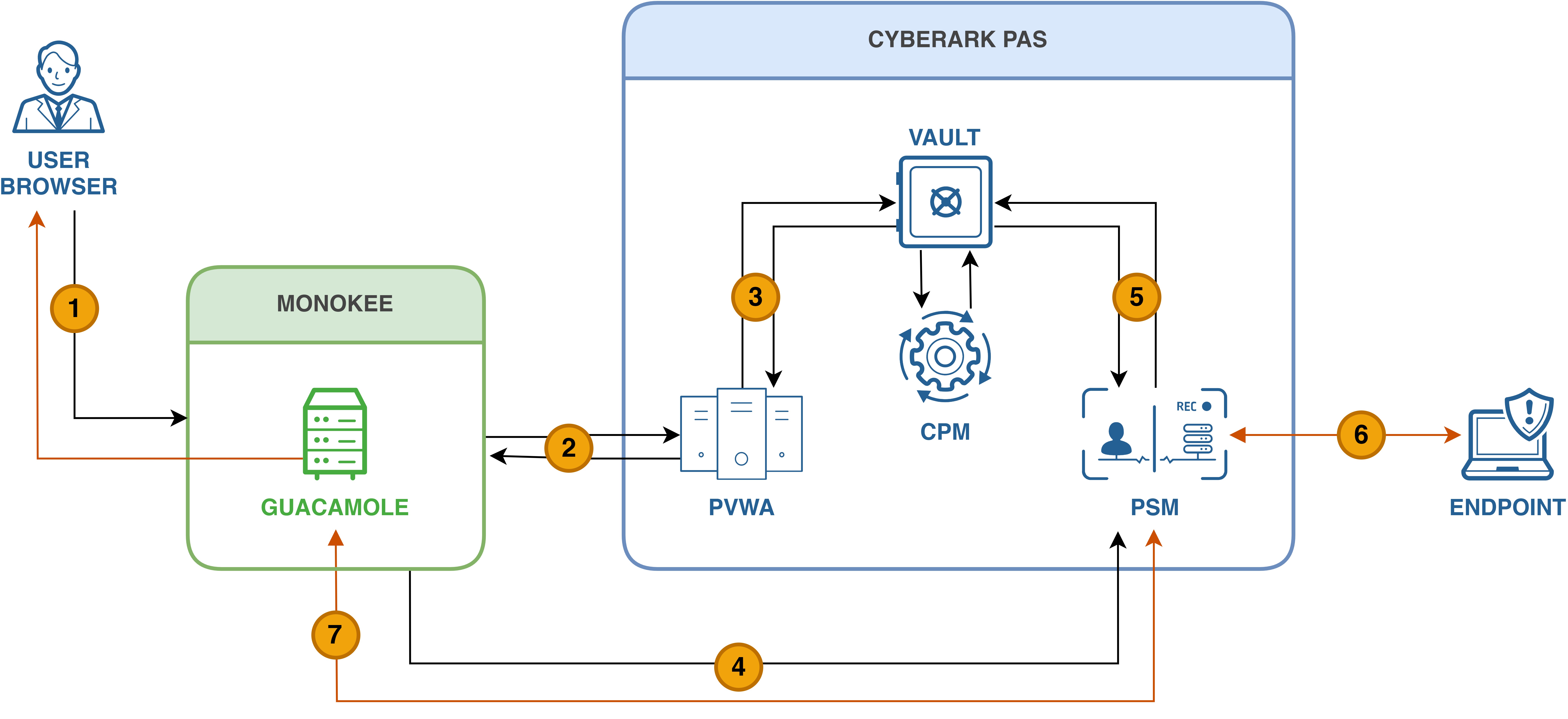
The figure describes the following:
- The user logs in to monokee using a browser and asks for a CyberArk application.
- Monokee makes a REST request to the API Server provided by the PVWA module and passes to it the credentials of CyberArk login that belongs to the Monokee’s User Identity.
- The Vault checks if the API login request is valid and returns all connection targets of the vault user.
- The monokee user starts a new connection through Guacamole to the PSM and passes to it the CyberArk token authorization.
- PSM receives the RDP token authorization and checks if is valid in the Vault.
- The token was successfully confirmed and the RDP tunnel session from the Endpoint target to the PSM is opened.
- The RDP session from the PSM is redirected to Guacamole and then sent back to the user browser in a new tab.
