Monokee offers a potent solution with robust capabilities that are in line with the fundamental IGA functionalities. It provides inherent support for identity lifecycle management, ensuring that users have appropriate access when needed. The access request processes are streamlined, powered by the V.I.O. to further enhance access control and identity management. Monokee also features inherent capabilities for basic analytics and reporting, offering valuable insights into user activity and access patterns.
While Monokee excels in these fundamental areas, there are some standard IGA functionalities that are currently not implemented. However, Monokee’s strength lies in its ability to integrate with clients’ existing tools and other vendors. This ensures a comprehensive IGA solution that meets compliance requirements and covers all necessary functionalities. Through integration and collaboration, Monokee delivers a flexible and adaptable IGA system tailored to your organization’s unique needs, thus integrating with other parties to provide access certification, native auditing, enforcement of segregation of duties, role mining, and entitlement management. We are committed to providing effective and efficient IGA solutions and are here to assist with any further inquiries about Monokee’s capabilities and integrations.
In summary, Monokee provides a robust foundation for IGA, addressing key aspects of user lifecycle management, access control, and reporting needs. As we continue to evolve, the incorporation of additional standard functionalities like access certification will further strengthen Monokee’s position as a versatile IGA solution.
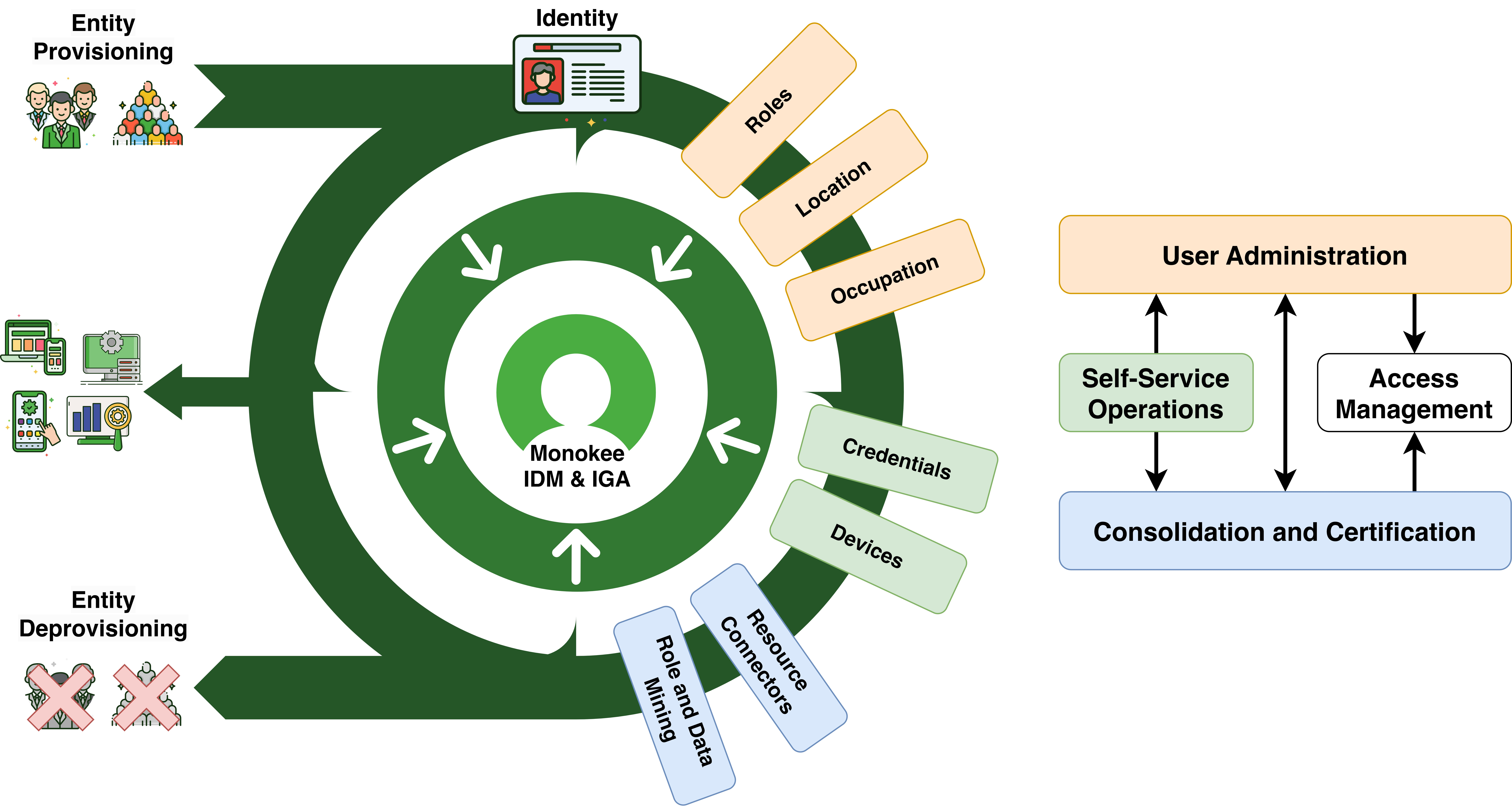
The IdM module focuses on enabling user management and general access privileges, while enabling native provisioning and deprovisioning for both users and applications. Together with the AM, the V.I.O., and the audit and reporting modules Monokee ensures that user identities and access privileges are aligned with business policies and regulations.
Critical Capabilities
Identity lifecycle management
Automatically create and delete user accounts in all relevant systems based on external and internal signals. Users, roles, groups, attributes, and applications can be managed via direct interaction with the platform or by creating custom workflows with the V.I.O.
Engineers and administrators have a full suite of pre-made connectors for third-party technologies, including, among others, Microsoft Active Directory and generic LDAP directories. Monokee Identity Manager acts as a bridge connector between multiple authoritative sources and unlimited target resources.
Administrators and engineers can define mappings between data structures from multiple authoritative sources to Monokee Identity and, from this, to the target resources. The custom flows orchestrated by the V.I.O. enable event-based data streams from the authoritative sources to the target resources. The native integration with all major technologies permits managing users, groups, attributes, and applications from any source and with any protocol. It includes role-based access control (RBAC) with the addition of custom attributes, which are key-value pairs that can be used to describe users and groups in more detail, enabling a complete ABAC-compliant approach to authorization. Values can be assigned statically by administrators or calculated dynamically during the user journey.
Access request process
Monokee’s Identity Manager streamlines access request workflows through the usage of the V.I.O. components. It offers pre-configured templates for various access needs, including applications, roles, functionalities, users, entitlements, and custom requests. These templates, which can be assigned to specific groups or users within the IGA framework, guide users through the request journey, simplifying the process and reducing administrative burden.
The system also features role-based access control, ensuring that the right individuals approve requests based on their roles and responsibilities. Users can start and complete access requests directly within the Monokee interface or through a dedicated request page, empowering them to manage their access needs actively.
Upon submission, an automated email notification is sent to designated approvers, streamlining communication and facilitating timely approvals. Approvers can access individual requests through the notification or process them in bulk, enabling efficient review and decision-making.
Monokee’s access request functionality is designed with the aim to lessen manual effort and enhance efficiency. It strives to uphold security best practices and minimize the risk of unauthorized access. The user experience is a key focus, with an intuitive interface and self-service capabilities, with an overall approach that provides a comprehensive and user-centric solution for IGA.
Analytics and reporting
An essential aspect of the Identity Manager module is the high-level overview of the insights and recommendations. The current version of Monokee's Executive Dashboard includes generic metrics such as the number of users, groups, roles, applications, and user journeys. It also has a sneak peek of access requests and logs to identify issues quickly. Future releases include enhanced review capabilities of policies and compliance status alongside general risk assessment indicators to help executives and administrators identify and prioritize the organization's IAM risks, review user access, logs, and applications regularly ensuring users only have access to the necessary resources.
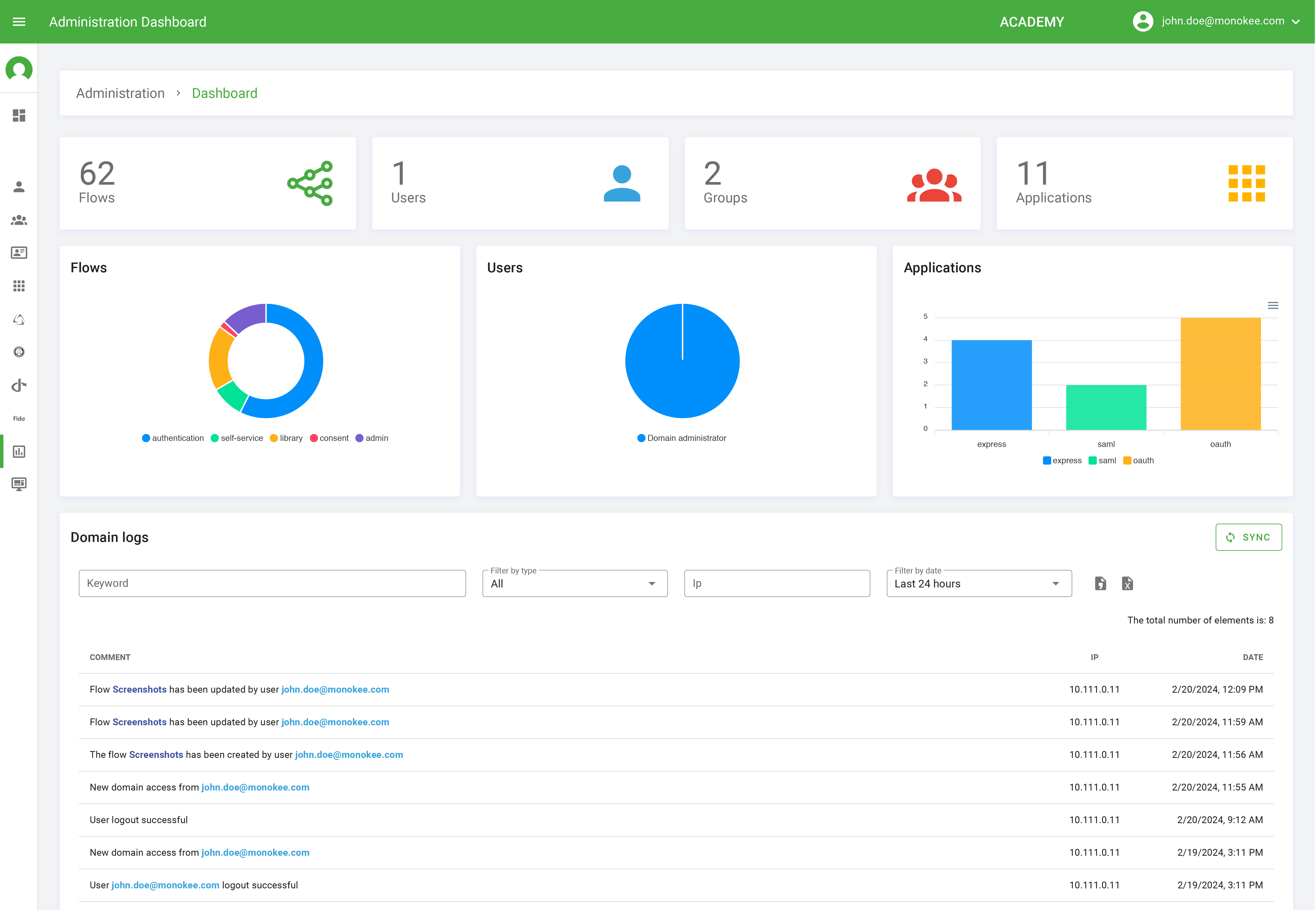
Planned reports and experimental data mining functionalities will enable insights and a data-driven approach to identity management. Custom functionalities will enable exploratory analysis of targets' data, including historical data related to identity and non-identity signals.
Policy and role management
Monokee supports ABAC, which allows organizations to define access control policies based on user attributes, such as job title, department, location, and occupation. Administrators can use these attributes to create more granular and flexible access control policies.
Provisioning via automated connectors
Ingest data from multiple authoritative directory services with native connectors and write to target resources and non-authoritative repositories. Mapping, consolidation, propagation, and general tasks are handled by the custom workflows in the Visual Identity Orchestrator. Experimental features allow for exploratory analysis of target resources and non-authoritative resources for insights and certification campaigns.
Monokee helps administrators manage employees, improving the efficiency, security, and compliance of their HR and administrative processes related to the lifecycle of user identities, even when users' identities change. For example, on changes in employees' roles, locations, or occupations, the Monokee can automatically update the employee's group membership, role assignments, and access policies.
Workflow orchestration
Multiple workflows can be designed to cover administrative processes such as onboarding, offboarding, and reconciliation campaigns, including automated KYC and AML steps or manual review. General compliance-oriented workflows are available to cover regulations requirements (GDRP and similar). Full traceability and real-time monitoring of processes and workflows ensure complete accountability. Self-service automation of end-user-facing interfaces enables a cost reduction in ticketing and help-desk activities. With Monokee's VIO, it is possible to achieve complete automation in self-service functionalities, including the transition to passwordless or application request. Monokee's Visual Identity Orchestrator (V.I.O.) allows administrators to design custom governance workflows for any identity-related task. For example, it is possible to create administrative workflows for onboarding, offboarding, and managing general access privileges, but also create self-service workflows to offload first-level ticketing for user support, including registration, password management, application access requests, and more. Monokee supports direct provisioning for third-party applications through SCIM, Just-In-Time provisioning, or customized API calls.
Additional Capabilities
Patented multi-domain tenants
Monokee’s patented feature allows administrators to manage multiple isolated domains within the same tenant. Rather than managing a unique data source for users, identities, flows, and so forth, Monokee enables strong segregation between domains. For example, the IT department of a company can manage a tenant for the whole organization, while each other Business Unit (BU) is independent and completely isolated. However, the IT department might have specific privileged accounts that are enabled to travel across the other domains, thus allowing seamless interaction with the platform and streamlined configurations. Domains can be joined in trusted relationships to enable seamless identity traveling between them (e.g., Administrators might manage both domains with different privileges and roles but with the same identity). These accounts are called Siblings. Data segregation and isolation can be guaranteed by logically separating the data sources (i.e., using different cryptographic keys to protect the data) or using different data clusters.
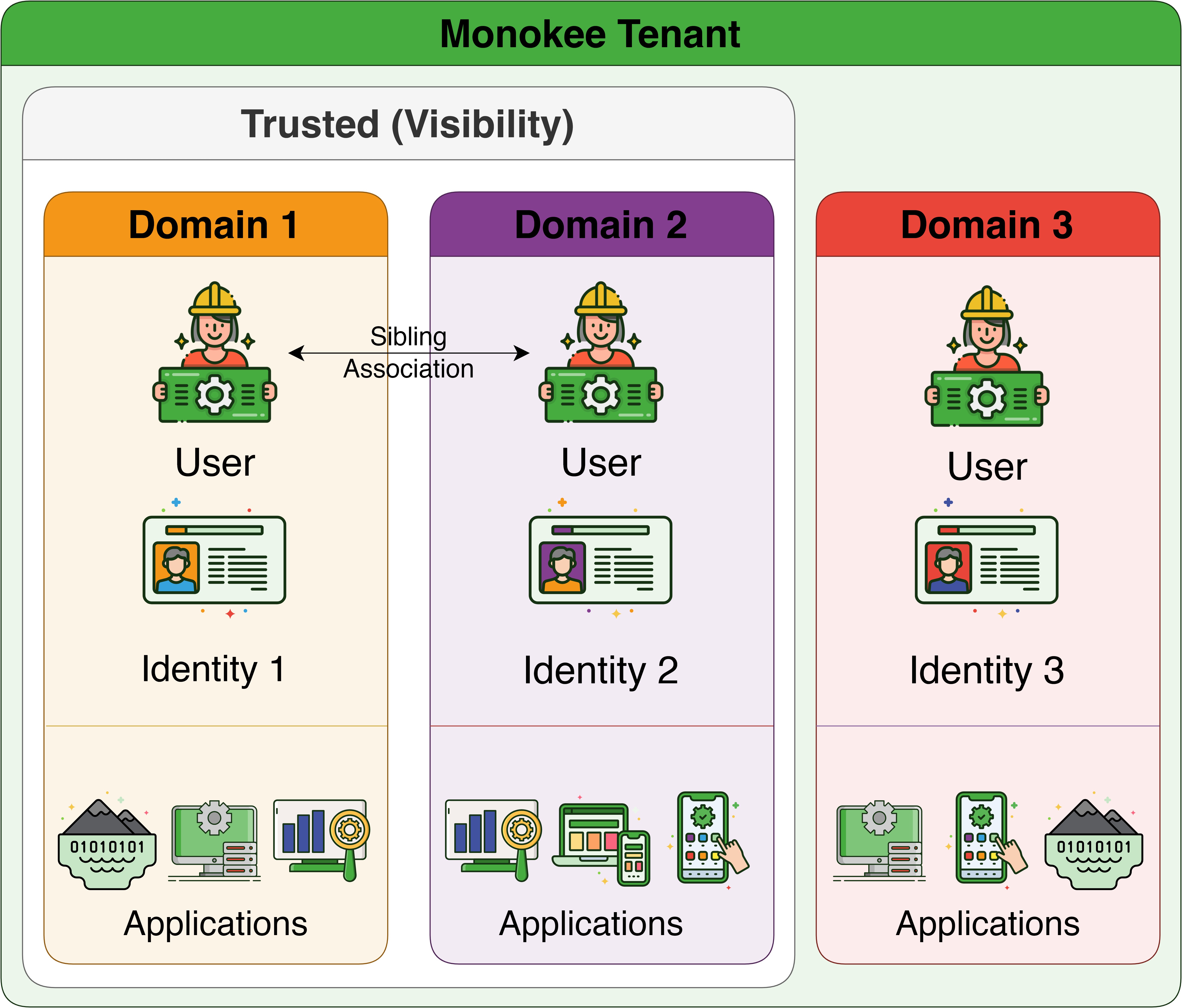
The patent US11799870B2 is titled "System and method for the management of multi-domain access credentials of a user able to access a plurality of domains." It is designed for managing multiple-domain access credentials of a user who is enabled to access a plurality of domains, including a credential management server where access credentials of the user are separately present for each of the domains and each of the access credentials includes the access level of the user for each of the domains. Identity registration and profile management Monokee supports a diverse range of sources, nonetheless, native functionalities for identity registration, management, and general user-facing profile management procedures are available out-of-the-box. This includes the registration and profile management of users who fall outside the purview of traditional HR systems, such as contractors, partners, external collaborators, or social login users. Monokee custom attributes are designed to capture not just basic profile information, but also custom properties that are specific to different user types and their access needs.
To reduce IT workload and improve user experience, Monokee empower users with self-service capabilities, allowing them to register, update profiles, and manage preferences themselves (including scopes, consent, and terms of service). Data validation and governance are critical to ensure data accuracy and compliance with regulations, and they can be achieved through validation rules and access controls for profile information. Furthermore, Monokee seamlessly integrates with third party systems like CRM and ERP to synchronize relevant user data and attributes.
Integration with authorization tools for contextual decisions
Monokee provides open APIs and support for standard protocols like SCIM to facilitate smooth integration with various authorization tools. This enables Monokee to share relevant user attributes and access context seamlessly with third-parties tools, thereby enabling dynamic access decisions based on real-time conditions. Monokee supports both RBAC and ABAC policies that consider user attributes, device information, location, and other contextual factors or non-identity signals for fine-grained access control. Centralized policy management in the V.I.O. enables administrators to manage and define access policies, regardless of the specific authorization tool used. Additionally, Monokee tracks and audits how user attributes and context are used in access decisions for transparency and compliance. Custom loggers can be deployed to measure and profile any step of any process.


