The term "identity orchestration" has become a popular buzzword, but its broad scope can sometimes lead to confusion. It encompasses a wide range of activities, from streamlining user journeys to integrating complex backend systems. This lack of clear definition can make it difficult for organizations to understand exactly what capabilities fall under this umbrella.
Monokee recognizes this need for disambiguation.
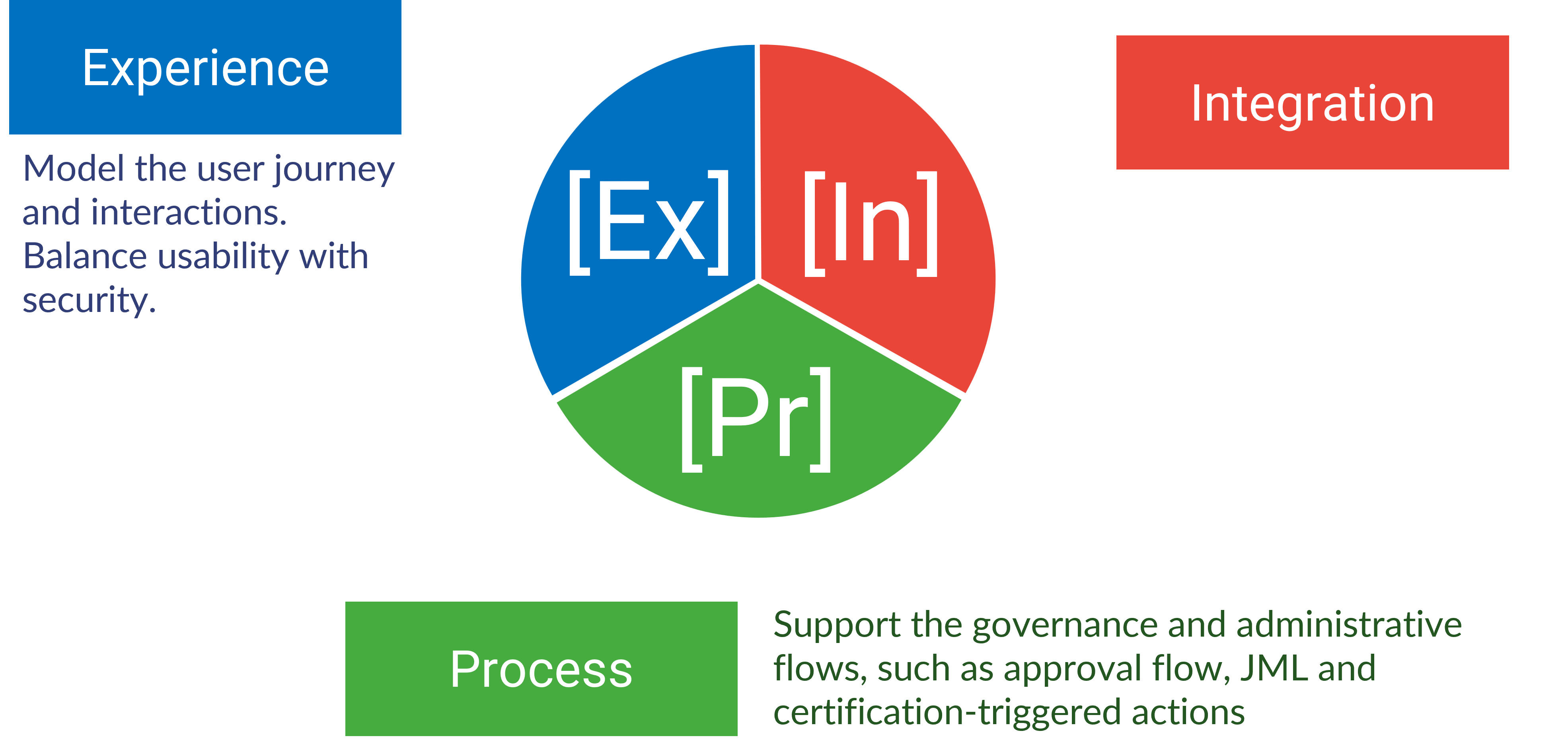
By breaking down identity orchestration into three distinct pillars – user experience, system integration, and enterprise process orchestration – we provide a clearer picture of the specific functionalities encompassed within this concept. This multi-faceted approach allows us to offer our clients targeted solutions that address their unique identity management needs.
Monokee identifies six enabling technologies for Identity Orchestration: a) User Journey Orchestration, b) Access Management, c) No/Low Code, d) Governance, e) Identity Consolidation, f) Decentralized Identities
Monokee's three pillars of the Identity Orchestration
User Experience
This pillar focuses on streamlining the user journey through access requests and application access. Monokee achieves this through the V.I.O., by customizing the user journeys with a WYSIWYG approach. Among other capabilities, the V.I.O. enables the introduction of context-aware challenges to the user, dynamically adjusted authentication requests based on user context (e.g., location, device). For example, a user logging in from an unfamiliar location might require MFA, while a trusted device at the usual workplace might only require a password. It also includes flows such as the lifecycle management self-service flows, for example to empower users to manage their profiles, update information, and request access to applications independently, reducing reliance on IT support and minimizing delays.
System Integration
This pillar deals with seamless connections between Monokee and various systems within an organization's IT infrastructure. Monokee facilitates this through pre-built connectors included in the node library, thus ending the necessity for complex manual integrations. Being API-driven further enhances this capability, as developers can integrate Monokee’s flows with ease by performing RESTful API calls to its flows, ensuring interoperability across diverse systems. Most protocols and standards are supported natively by Monokee, thus allowing companies to leverage existing digital identities from different providers.
Enterprise’s Processes
This pillar focuses on aligning user identity management with the organization's established workflows and business processes. Firstly, Monokee allows for high-level overview of JML processes directly from within the V.I.O., allowing unprecedented visibility and explainability of user lifecycle management tasks like onboarding, provisioning, and offboarding. These workflows can be triggered by events within Monokee or external systems, ensuring identities are managed in sync with business processes. Additionally, Monokee can dynamically adjust user access permissions based on real-time factors. This can involve integrating with HR systems to automatically revoke access upon employee termination or utilizing risk-based authentication to adapt security measures based on user context.
Enabling capabilities
User Journey Orchestration
While the term "journey time orchestration" might not be ubiquitous, its core principle – optimizing user experience within specific access management processes – holds immense value for building a strong identity fabric and driving user engagement within an enterprise. By orchestrating user journeys, organizations can create a unified identity fabric. This fabric leverages user context (location, device, previous logins) to dynamically tailor the authentication process. For instance, a user accessing a low-risk application might only require a simple password, while accessing confidential data might trigger MFA. This context-aware approach simplifies low-risk access while maintaining robust security for sensitive resources. Furthermore, user journey orchestration empowers self-service options. Users can manage profiles, reset passwords, or request access to applications independently, reducing reliance on IT support and minimizing delays. This not only streamlines processes but fosters a sense of control and ownership over their identities within the organization. For the user experience side, Monokee leverages its UX expertise and loop-in design to tailor the login process based on user context data (location, device, etc.) This eliminates the frustration of vastly different interfaces across various systems. Monokee achieves this through a visual, block-like user journey solution that allows for real-time decision-making based on user context, ensuring a smooth and secure experience. Furthermore, Monokee understands the complexities of integrating diverse systems. With extensive experience in system integration and digital transformation, Monokee offers a solution that simplifies the process. The visual orchestrator acts as a central hub, providing a bird's-eye view of all connected systems and streamlining the overall user journey orchestration experience.
Access Management
Access management acts as the bedrock for all three pillars of orchestration within Monokee's identity management platform. It plays a critical role in two key aspects: a unified platform for diverse identities and streamlined user journeys. Monokee's access management capabilities excel at integrating various user identities, encompassing modern cloud identities, legacy on-premises systems, and even portable identities from external providers. This creates a centralized platform to manage access across these diverse sources, significantly simplifying orchestration efforts. Administrators can leverage Monokee to manage access controls and user journeys seamlessly, regardless of the underlying identity source. Additionally, effective access management ensures users experience only the necessary authentication steps based on their context and access request. This eliminates unnecessary complexity and streamlines user journeys, fostering a smoother overall experience. Monokee achieves this through features like adaptive MFA and context-aware authentication. These features dynamically adjust security measures based on real-time factors (location, device, etc.), ensuring a balance between security and user experience within the orchestrated journey.
No/Low Code
Monokee understands that traditional code-first approaches to UX design can be time-consuming and resource-intensive, especially in projects involving multiple technology stacks. The V.I.O.'s visual UX builder with its pre-built, modern UX templates addresses this challenge. Indeed, the low/no-code functionality plays a vital role in enabling all three pillars of orchestration within Monokee's identity platform. Traditionally, orchestration workflows required extensive coding expertise, limiting accessibility for many organizations. Monokee's Low/No-Code approach through its V.I.O. empowers a wider range of users to take part in orchestration tasks. Business analysts and IT professionals with less coding experience can leverage the drag-and-drop interface to configure, personalize, and refine user journeys. This not only reduces reliance on specialized developers but also fosters collaboration between different teams within the orchestration process, improving the agility and efficiency of the enterprise’s response to changes.
Governance
Identity governance acts as a critical enabler for all three pillars of orchestration within Monokee's identity management platform. Effective identity governance ensures consistent and aligned management of user identities, access controls, and workflows across the enterprise stack, effectively minimizing inconsistencies and security gaps that could arise from managing identities in silos. By creating visual policies, access controls, and audit trails, Monokee helps organizations maintain control over user identities and access privileges. Monokee recognizes that traditional identity management solutions can lock organizations into specific vendor processes. This can hinder orchestration efforts when integrating diverse systems. Monokee empowers organizations to define and configure identity governance rules and workflows that seamlessly integrate with various systems, regardless of vendor, prioritizing vendor neutrality and allowing organizations to adapting to changes without external intervention. Monokee helps organizations avoid the creation of "impractical or useless data lakes" by ensuring data collected through identity governance processes is relevant, secure, and serves a defined purpose, providing a framework for setting up clear and auditable data access controls.
Identity Consolidation
Disparate identity data and processes across various systems can hinder workflow automation within orchestration. Monokee's consolidation approach tackles this by providing a solution that makes Joiner/Mover/Leaver processes interpretable by all involved stakeholders. By creating a unified and transparent identity layer, Monokee allows organizations to document, standardize, and consolidate identity-related workflows across different systems by providing a framework that promotes explainability and interpretability of the processes. Furthermore, Monokee streamlines the consolidation of identities and access controls across systems with different protocols and data formats by leveraging the plug-and-play nature of the Identity Management module. Identities, often derived from multiple inconsistent trust authorities, can be centrally managed and efficiently maintained with the orchestration workflows.
Decentralized Identities
Monokee acknowledges the challenge of a digital divide when introducing decentralized identities within an enterprise ecosystem, indeed this transition is a significant change in user identity management. By enabling users to use their government-issued digital identities for authentication across various applications, Monokee can facilitate a smoother and more self-sovereign user experience. Monokee offers multiple integrations with third-party digital wallets, providing users with familiar interfaces that simplify the adoption of decentralized identities within the user journey orchestration process. Integrations that often require burdensome infrastructure changes alleviated by the pre-configured nodes available in the V.I.O.
Visual Identity Orchestrator (V.I.O.)
At its core, Monokee features a complete orchestration tool for managing identities, applications, and user journeys. Monokee’s V.I.O. permits the planning and execution of user journeys for each application. These flows can be monitored and analyzed to infer security properties and statistical information. Security engineers can dynamically adapt them to organizations’ requirements and ecosystem changes. By using the V.I.O., security engineers and administrators can reduce development and operational costs while increasing usability and awareness.
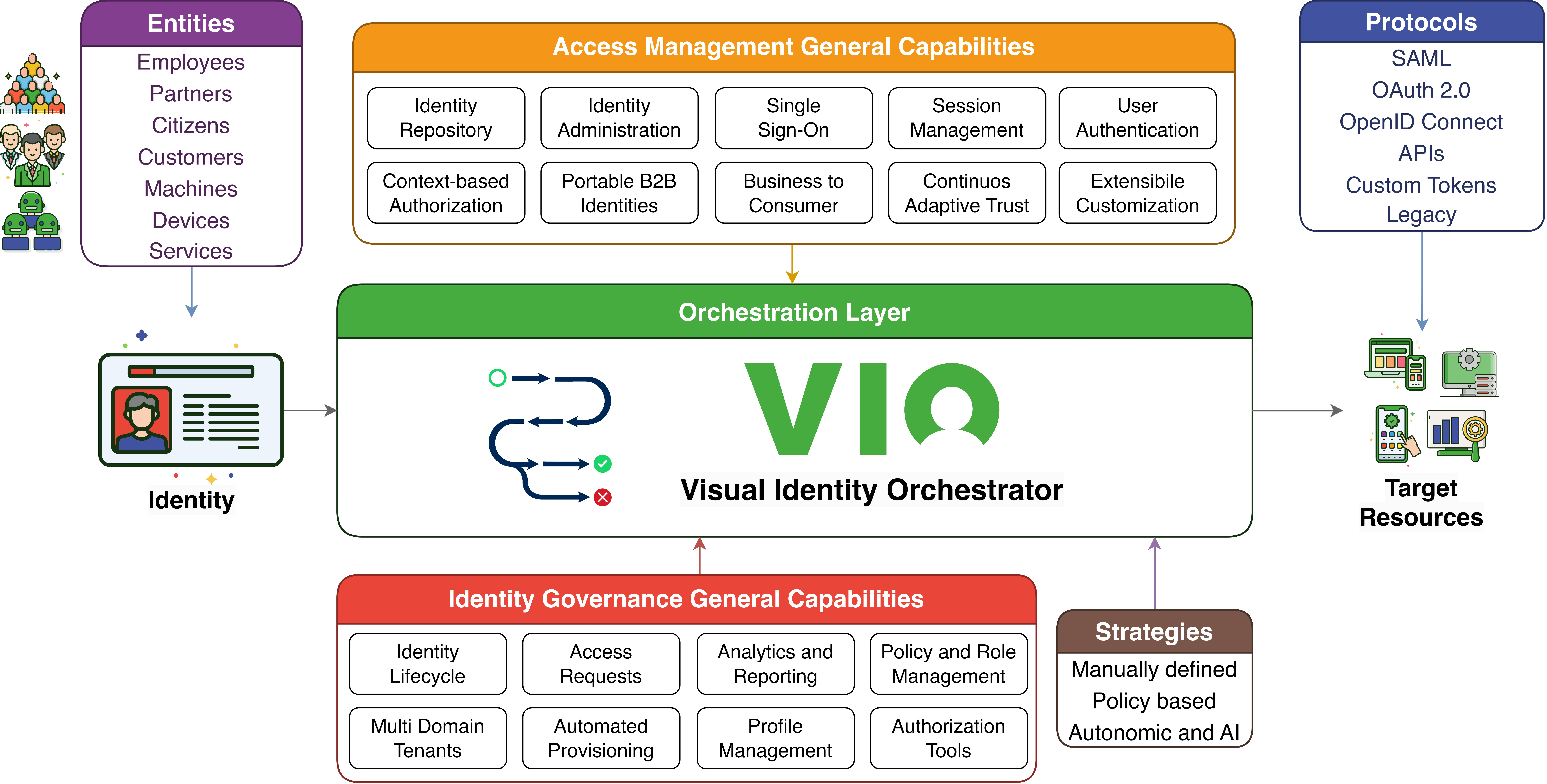
Monokee Visual Identity Orchestrator helps organizations achieve and maintain compliance with regulations such as GDPR, HIPAA, and PCI DSS by providing centralized visibility into user access across all systems and applications. The V.I.O. also helps organizations avoid compliance infractions and make the audit process more straightforward and transparent.
Monokee’s V.I.O. is a solution that scalable to grow with organizations as they adopt new systems and applications, ensuring that access management remains efficient without additional manual effort. By supporting a range of authentication and authorization frameworks, it allows organizations to choose the methods and approaches that work best for their environment and integrate with a variety of systems and platforms.
For users, the V.I.O. can provide a more seamless and intuitive registration and login process by removing some of the friction that users have traditionally faced during the identification and authentication process, such as providing proof of identity, verifying contact information, and auto-filling forms for billing information. With just one set of login credentials (ideally not even those) to manage, users can be more productive by spending less time on login and registration.
Overall, Monokee’s V.I.O. provides organizations with:
- Compliance: Monokee V.I.O. helps organizations achieve and maintain compliance with regulations such as GDPR, HIPAA, and PCI DSS.
- Scalability: Monokee V.I.O. is scalable to grow with organizations as they adopt new systems and applications.
- Flexibility: Monokee V.I.O. supports a range of authentication and authorization frameworks.
- Enhanced Security: Monokee V.I.O. can help organizations improve their security posture by centralizing access control, automating security workflows, and providing visibility into user activity.
- Seamless User Experience: Monokee V.I.O. can provide a more seamless and intuitive registration and login process for users.
- Simplified Identity Governance: Monokee V.I.O. provides a unified platform for managing user identities and access privileges, making it easier for organizations to simplify their identity governance processes.
- Automation of Identity Processes: Monokee V.I.O. can automate a wide range of identity processes, such as user onboarding and offboarding, access provisioning and deprovisioning, and access reviews. This can help organizations to improve the efficiency, accuracy, and security of their identity management processes.
Each flow can be designed with a drag-and-drop canvas and connected to any given application. Custom blocks can be used to catch events of interest or specific conditions.