Monokee, a next-generation Identity and Access Management (IAM) platform, leverages its innovative Visual Identity Orchestrator (VIO) to streamline integrations with various identity providers. This technical deep-dive explores the seamless integration between Monokee and Microsoft Entra, enabling near-instantaneous user provisioning through a series of well-defined API calls – a stark contrast to the traditionally complex and time-consuming IAM integrations.
5 posts tagged with "Visual Identity Orchestrator (VIO)"
View All TagsSimple Identity Orchestration & Secure Face Verification On Any Device | iProov + Monokee
Monokee & iProov Partnership

Monokee and iProov are now collaborating to take another leap forward in authentication technology. We have seamlessly integrated iProov’s cutting-edge face verification capabilities as an innovative authentication method within Monokee’s low/no-code Identity and Access Management (IAM) identity orchestration platform.
In this article, we'll explain how iProov and Monokee's combined technologies work together to enhance security and user experience, creating a frictionless, passwordless option for enterprises.
Monokee 4.0 Access Management Capabilities
Monokee’s Access Management capabilities cater to both internal and external users, addressing use cases across a wide range of applications and services. It offers centralized identity management, single sign-on, multi-factor authentication, and granular authorization controls. These features align with external trends such as the convergence of IAM features, SaaS adoption, passwordless authentication, adaptive access, and cybersecurity mesh.
Monokee 4.0 Identity Orchestration
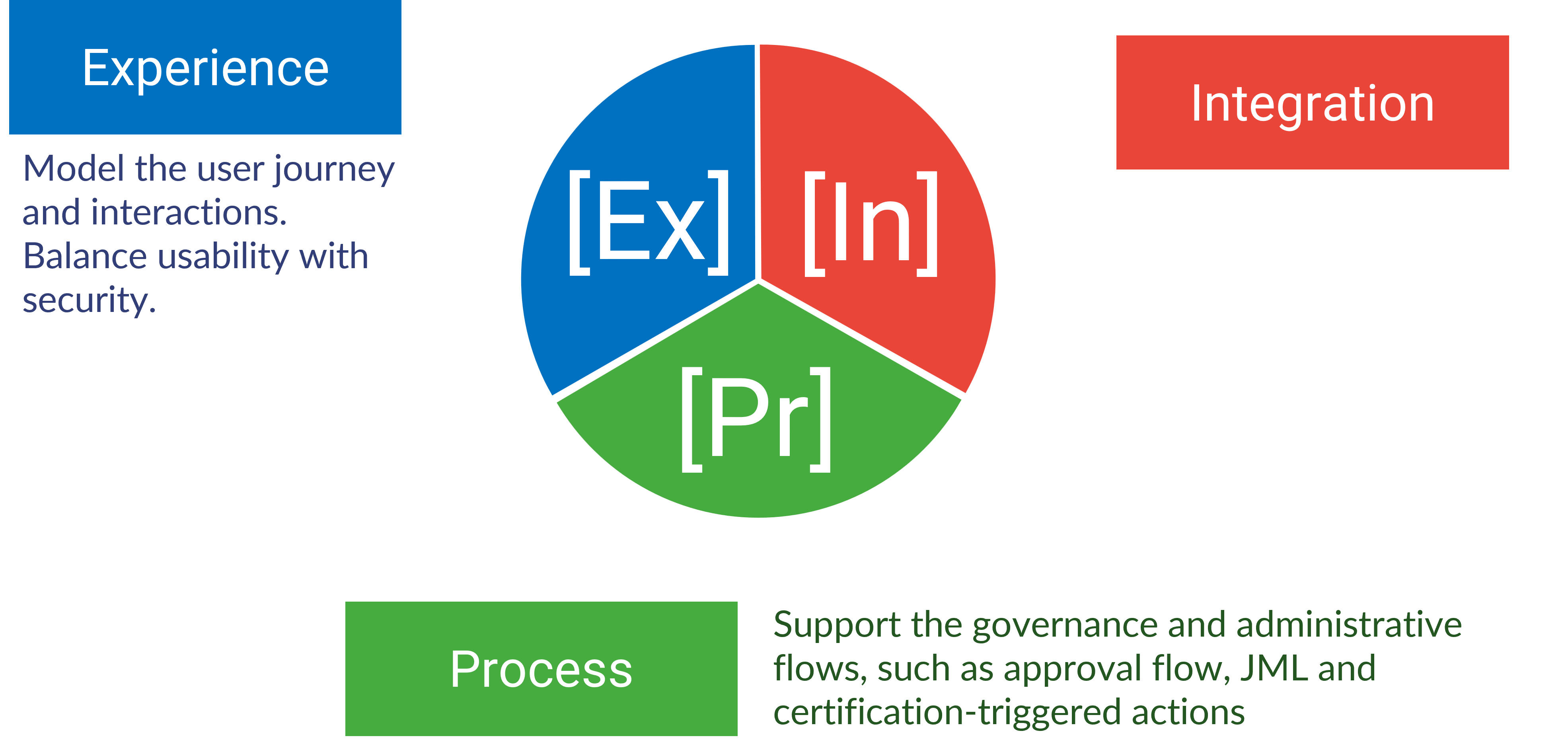
The term "identity orchestration" has become a popular buzzword, but its broad scope can sometimes lead to confusion. It encompasses a wide range of activities, from streamlining user journeys to integrating complex backend systems. This lack of clear definition can make it difficult for organizations to understand exactly what capabilities fall under this umbrella.
Monokee recognizes this need for disambiguation.
By breaking down identity orchestration into three distinct pillars – user experience, system integration, and enterprise process orchestration – we provide a clearer picture of the specific functionalities encompassed within this concept. This multi-faceted approach allows us to offer our clients targeted solutions that address their unique identity management needs.
Monokee identifies six enabling technologies for Identity Orchestration: a) User Journey Orchestration, b) Access Management, c) No/Low Code, d) Governance, e) Identity Consolidation, f) Decentralized Identities
Add Toothpic as new passwordless MFA solution
Monokee's partner: Toothpic
Toothpic stands at the forefront of revolutionary authentication technology, introducing a cutting-edge approach that leverages the unique hardware characteristics of smartphones for unclonable identity verification. At its core, Toothpic addresses the escalating challenges of traditional authentication methods and forges a path towards a frictionless, passwordless identity and access management (IAM) framework.



